ACF Security [Updates Review]
Table of Contents

In the intricate landscape of WordPress development, Advanced Custom Fields (ACF) emerge as a cornerstone, offering unparalleled flexibility in tailoring websites to specific needs. ACF empowers developers to create dynamic and content-rich WordPress sites, elevating user experiences. As the reliance on ACF grows, so does the imperative to fortify its security measures. ACF security is not merely a component; it is a linchpin in maintaining the overall security of a WordPress website. The sensitivity of the data managed by ACF necessitates a vigilant approach to thwart potential vulnerabilities and ensure a robust defense against evolving cyber threats.
In the realm of ACF, a pivotal moment has arrived with the release of version 6.2.5. This update is not just a routine enhancement; it is a crucial stride in reinforcing the security infrastructure of ACF-powered websites. In this context, we delve into the significance of ACF, underscore the critical role of security, and unravel the key aspects of ACF version 6.2.5 that demand our attention. Join us on this exploration as we navigate the intricate intersection of ACF, security, and the latest advancements in version 6.2.5.
At IT Monks, we incorporate ACF into our project launches and web development services, including Content Migration, API Integrations, WordPress Maintenance, Plugin Development, and Custom WordPress Development.
ACF Version 6.2.5 Security Update
The recent release of Advanced Custom Fields (ACF) version 6.2.5 brings a significant security update, underlining the commitment to the robustness of ACF-powered websites.

Explanation of the Security Fix
ACF version 6.2.5 addresses a crucial security fix, a meticulous response to potential vulnerabilities identified within the system. The update introduces strategic measures to enhance the overall security posture of ACF installations, providing a safeguard against emerging cyber threats. Before proceeding with any update, awareness is key. The importance of understanding the intricacies of the security fix cannot be overstated. Users and developers alike are urged to delve into the specifics of the update, grasping the nuances of the implemented changes. This knowledge ensures a smooth transition and empowers users to adapt their websites effectively to the new security measures.
Upcoming Changes in ACF Output for the_field
A noteworthy aspect of the ACF version 6.2.5 update is the alteration in the output behavior of the_field function. The update introduces a change wherein the ACF Shortcode output will be subject to the WordPress HTML escaping function wp_kses. This shift is a proactive measure to mitigate potential security risks associated with unescaped HTML output.
As users navigate this update, being cognizant of the upcoming changes in ACF output, particularly for the_field function, becomes paramount. This heightened awareness ensures seamless security update integration, minimizing disruptions in rendering ACF fields.
In essence, ACF version 6.2.5 is not merely an update but a commitment to continuously enhancing ACF security, fortifying the foundation of WordPress websites that rely on this powerful customization tool. Stay informed, stay secure, and confidently embrace the future of ACF.
Understanding ACF Security Risks

As the backbone of dynamic content customization in WordPress, Advanced Custom Fields (ACF) stands as a powerful tool. However, with this power comes the responsibility to safeguard against potential vulnerabilities and WordPress security threats unique to ACF implementation.
Identification of Potential Vulnerabilities
The intricate nature of ACF usage opens doors to potential vulnerabilities that, if not addressed, could pose security risks. From intricate data structures to diverse field types, each element introduces a layer of complexity that demands vigilant scrutiny. Identifying potential vulnerabilities involves meticulously examining how ACF interacts with user inputs, custom fields, and the broader WordPress ecosystem. ACF implementation is not immune to the diverse array of security threats prevalent in the digital landscape. Threats such as SQL injection, cross-site scripting (XSS), and unauthorized access can exploit weaknesses in ACF configurations, leading to data breaches and compromised websites. An in-depth understanding of these threats is paramount to developing effective countermeasures.
In this exploration of ACF security risks, the goal is to empower developers and users alike with the knowledge needed to fortify their ACF-powered websites. By identifying potential vulnerabilities and understanding common security threats specific to ACF, we pave the way for proactive security measures that uphold the integrity of WordPress websites and the valuable content they host. Stay tuned as we delve deeper into best practices and strategies to mitigate these risks and ensure a resilient ACF implementation.
Best Practices for ACF Security
In the realm of Advanced Custom Fields (ACF), robust security practices are paramount to safeguarding the integrity of your WordPress website. Below you will find the fundamental aspects of ACF security,each playing a crucial role in fortifying your ACF implementation.
1. Secure Configuration
Optimal ACF Settings:
- Begin by configuring ACF settings with a security-first mindset. This involves fine-tuning settings to align with your website’s specific security requirements.
- Explore ACF options related to data storage, permissions, and accessibility, ensuring they adhere to industry best practices and your website’s unique security needs.
User Permissions Management:
- Implement strict user permission controls within ACF. Define roles and permissions carefully, limiting access to ACF settings and configurations only to those who genuinely require it.
- Regularly audit and update user permissions, revoking unnecessary access and minimizing the potential attack surface.
Best Practices for ACF Field and Group Naming Conventions
Descriptive Yet Secure Field Names
- Choose field names that are not only descriptive but also considerate of security. Avoid using overly generic names that could be easily guessed by potential attackers.
- Incorporate a combination of letters, numbers, and symbols in field names to enhance their complexity and resist brute-force attacks.
Use of Prefixes and Suffixes
- Implement prefixes or suffixes to uniquely identify ACF fields associated with your website. This practice helps organize your fields and minimizes the risk of naming conflicts with other plugins or themes.
- For added security, consider incorporating a site-specific prefix to ensure uniqueness and avoid clashes with other elements in the WordPress ecosystem.
Consistent Naming Conventions
- Enforce consistent naming conventions for ACF fields and groups across your website. This not only enhances readability for developers but also contributes to a standardized and secure structure.
- Document your naming conventions to maintain clarity and facilitate collaboration among multiple developers working on the same project.
2. User Permissions
- Role-Based Access: Tailor user permissions based on roles to grant appropriate levels of access. For instance, administrators may have full control, while editors and authors might have limited access.
- Least Privilege Principle: Adhere to the principle of least privilege, granting users the minimum permissions necessary for their tasks. Avoid providing unnecessary access to ACF features.
Restricting Access to ACF Settings and Configurations:
- Utilize Capability Checks: Leverage WordPress capability checks to control access to ACF settings. Ensure that only users with the requisite capabilities can modify ACF configurations.
- Custom Capabilities: If needed, create custom capabilities specific to ACF settings. This allows for fine-grained control over who can perform particular actions within the ACF ecosystem.
- Plugin and Theme Integration: Integrate user permission checks seamlessly with your plugins and themes to maintain consistency in access control across the entire WordPress environment.
- Audit User Access: Regularly audit user access to ACF settings to identify and address any anomalies or unauthorized configurations.
3. Implementing Robust Data Validation
The foundation of ACF security begins with stringent data validation practices. This involves scrutinizing user inputs, custom field values, and any data flowing into the ACF system. By validating data at the point of entry, developers can ensure that only permissible and expected values are accepted, mitigating the risk of malicious inputs that could exploit vulnerabilities. Utilizing predefined rules, regular expressions, and custom validation functions, developers can establish criteria for the types and formats of data accepted by ACF fields. This proactive approach significantly reduces the likelihood of security breaches stemming from improperly formatted or unexpected data.
Utilizing Sanitization Functions
Sanitization acts as a secondary defense layer, providing an additional shield against potential security threats. Even with robust validation in place, it’s essential to sanitize data before it gets stored or processed further within the ACF system. Sanitization functions help cleanse data of any potentially harmful elements, such as special characters, HTML tags, or script injections.
ACF supports various sanitization functions, including those native to WordPress and custom functions tailored to specific security needs. Leveraging these functions ensures that data undergoes thorough cleansing, promoting a secure data environment within ACF.
Utilizing ACF Security Plugins

Let’s explore an overview of five notable ACF security plugins available in the WordPress ecosystem, comparing their features and functionalities. Additionally, we’ll provide a step-by-step guide on integrating and configuring ACF security plugins to enhance protection.
1. ACF Content Analysis for Yoast SEO
Integrates with the popular Yoast SEO plugin to analyze ACF content for SEO optimization.
Features:
- Content analysis for ACF fields.
- Compatibility with Yoast SEO.
2. ACF Theme Code for Advanced Custom Fields
Generates theme-specific code for ACF fields, streamlining integration.
Features:
- Automated code generation for theme integration.
- Customization options for field output.
3. ACF Advanced Forms
Expands ACF capabilities with advanced form-building features.
Features:
- Custom form creation for ACF fields.
- Conditional logic and field validation.
4. ACF Better Search
Improves the search functionality of ACF fields for better user experience.
Features:
- Enhanced search capabilities for ACF content.
- Compatibility with default WordPress search.
Each plugin offers distinct features catering to specific ACF requirements. The choice depends on the unique needs of the website, such as SEO optimization, frontend display preferences, theme integration, form creation, or search enhancement.
Step-by-Step Guide on Integration and Configuration
- Plugin Installation:
- Navigate to the WordPress dashboard.
- Go to ‘Plugins’ and click ‘Add New.’
- Search for the desired ACF security plugin.
- Click ‘Install Now’ and then ‘Activate.’
- Configuration Settings:
- Access the plugin settings from the WordPress dashboard.
- Configure general settings based on your security preferences.
- Explore additional features and customize as needed.
- Integration with ACF:
- Ensure ACF is installed and activated.
- Navigate to ACF settings and locate the integration options for the chosen plugin.
- Follow on-screen instructions to integrate ACF with the security plugin.
- Testing and Optimization:
- Conduct thorough testing to ensure seamless integration.
- Optimize plugin settings based on website requirements.
- Monitor and update plugins regularly for enhanced security.
ACF and Cross-Site Scripting (XSS) Mitigation

Cross-Site Scripting (XSS) vulnerabilities pose a significant threat in the web development landscape, and Advanced Custom Fields (ACF) is not immune. To fortify ACF against potential XSS risks, it’s crucial to comprehend the role ACF plays in these vulnerabilities and implement effective mitigation measures. Additionally, testing and validating ACF implementation against XSS threats are integral steps in ensuring a secure web environment.
ACF, by design, allows users to input and display custom content, making it susceptible to XSS vulnerabilities. Malicious actors may attempt to inject scripts or harmful code into ACF fields, posing a risk to website visitors. Understanding this inherent risk is the first step toward crafting robust defenses.
Implementing Measures to Mitigate XSS Risks
Input Validation
Enforce strict validation rules for ACF inputs, allowing only permitted data formats and rejecting any potentially harmful content.
Output Sanitization
Employ thorough output sanitization to strip any unauthorized or malicious code from ACF-generated content before rendering it on the website.
Context-Aware Escaping
Apply context-aware escaping methods to ACF output, ensuring that the appropriate escaping functions are used based on the specific context of data usage (e.g., HTML, JavaScript, URLs).
Content Security Policy (CSP)
Implement a robust Content Security Policy that defines trusted sources for scripts, styles, and other resources, minimizing the risk of unauthorized script execution.
Regular Security Audits
Conduct routine security audits to identify and rectify potential vulnerabilities in ACF implementation. Automated tools and manual code reviews can be instrumental in this process.
Testing and Validating ACF Implementation Against XSS Threats
Automated Scanning
Utilize automated security scanning tools to identify common XSS vulnerabilities in ACF code. These tools can quickly highlight potential weaknesses for further investigation.
Manual Penetration Testing
Engage in manual penetration testing to simulate real-world scenarios where malicious actors attempt to exploit ACF vulnerabilities. This hands-on approach allows for a comprehensive understanding of potential risks.
User Input Testing
Conduct exhaustive testing with a variety of user inputs, including special characters and script injections, to evaluate how ACF handles different types of content.
Real-Time Monitoring
Implement real-time monitoring for ACF-generated content to detect and respond promptly to any suspicious or malicious activities.
ACF and Database Security

Securing ACF data storage within the WordPress database is paramount for maintaining the integrity of the overall system. Configuring database permissions for ACF tables and fields is a crucial aspect of this security endeavor.
Securing ACF Data Storage
Ensuring the security of ACF data stored in the WordPress database involves implementing robust measures to protect against unauthorized access and potential breaches. Developers should:
- Encrypt sensitive ACF data within the database to add an additional layer of protection.
- Limit access to ACF tables and fields only to authorized users and applications.
- Regularly review and update database connection strings to mitigate the risk of SQL injection attacks.
Configuring Database Permissions for ACF Tables and Fields
Fine-tuning database permissions is essential for limiting access and permissions to ACF-related tables and fields. Developers can:
- Assign the principle of least privilege, granting users only the permissions necessary for their specific roles.
- Utilize database management tools to set specific permissions for ACF tables, restricting unauthorized modifications or access.
- Regularly audit and adjust permissions based on changes in user roles or organizational structure.
Regular Database Audits
Regularly auditing the database is a proactive measure to identify and address potential security gaps. This involves:
- Conducting periodic database access logs reviews to identify suspicious or unauthorized activities.
- Verifying the integrity of ACF data within the database to ensure that it aligns with expected formats and values.
- Implementing automated tools for database scanning and vulnerability assessments.
By embracing a continuous auditing process, developers can swiftly detect and respond to any anomalies in ACF database security, fortifying the overall resilience of the WordPress ecosystem.
One Click Update
You can easily update the Advanced Custom Fields plugin through the ‘Plugins’ page in your WordPress website admin area. When updates are available, you’ll see them on this page and can apply them by clicking the “update now” button.
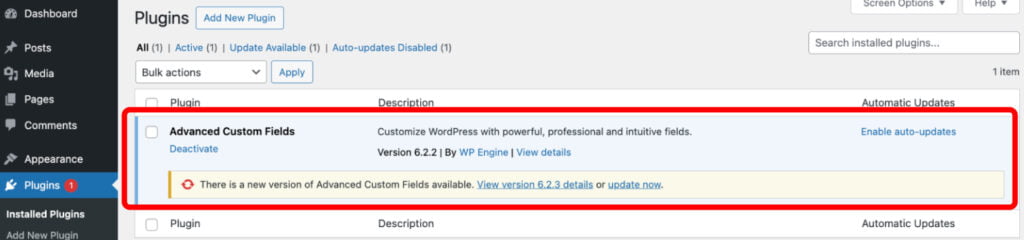
This method also applies to ACF PRO, but only if there’s an active license. Simply enter the license key on the ‘ACF -> Updates’ admin page to do this.
If your license hasn’t been activated and an update is ready, you’ll receive a notification when visiting the ‘Plugins’ page.
How to Update Manually
You can manually update the plugin by going to your WordPress admin’s ‘Plugins’ page. Click on Add New Plugin, and then select Upload Plugin to begin the process. The new version will replace the old one while keeping your fields and settings unchanged. You can get the Advanced Custom Fields plugin files from your account from the WordPress repository page and ACF PRO plugin files.
Alternatively, you can update plugins by copying and pasting their files into the ‘wp-content/plugins’ folder. Modifying these files won’t cause any data loss or change, so it’s safe to delete and re-upload a plugin folder if needed.
ACF Version 6.2.7 Preview
As part of the continuous commitment to improving security and functionality, ACF version 6.2.7 introduces significant changes to enhance the safety of websites built with Advanced Custom Fields (ACF). Let’s explore the key features and modifications to expect in this upcoming release.
1. Escaping Unsafe HTML in the_field() and the_sub_field():
One of the focal points of ACF version 6.2.7 is the introduction of enhanced security measures for the_field() and the_sub_field() functions. In this release, these functions will undergo automatic HTML escaping to mitigate the risk of potential Cross-Site Scripting (XSS) vulnerabilities.
By default, unsafe HTML will be stripped from the output, ensuring that only safe and sanitized content is rendered. This change aims to bolster the overall security of ACF implementations and protect against the injection of malicious scripts.
2. Notification Mechanism for HTML Changes
To facilitate a smooth transition for developers and administrators, ACF version 6.2.7 incorporates a notification mechanism. Users will be alerted when unsafe HTML is removed from a field value output by the ACF Shortcode, offering transparency about the changes made to enhance security.
This notification system is crucial in informing stakeholders about alterations in HTML output, enabling them to take proactive measures if needed. The transparency provided by these notifications aligns with ACF’s commitment to responsible and user-friendly security practices.
3. Proactive Security Measures:
ACF version 6.2.7 represents a proactive step towards securing ACF-powered websites by addressing potential vulnerabilities associated with HTML output. By automatically escaping unsafe HTML in the_field() and the_sub_field() functions, ACF aims to provide a more robust defense against XSS threats.
Developers are encouraged to review and adapt their codebase accordingly to align with the upcoming changes in ACF 6.2.7. The notification mechanism serves as a valuable tool in this process, ensuring that users stay informed about the security enhancements and can take any necessary actions to maintain the integrity of their ACF implementations.
In conclusion, navigating the realm of Advanced Custom Fields (ACF) in WordPress development demands a comprehensive approach that combines customization with robust security practices. Understanding and addressing potential vulnerabilities, such as Cross-Site Scripting (XSS), and securing ACF data within the WordPress database are critical for strengthening the integrity of ACF-powered websites. With the impending release of ACF version 6.2.7, developers and administrators should stay informed about the changes, particularly the automatic escaping of unsafe HTML in the_field() and the_sub_field() functions. This proactive step highlights ACF’s dedication to enhancing security and gives users the transparency needed to adjust their implementations accordingly.
IT Monks Agency closely monitors the latest releases and industry updates. Given that we utilize ACF in our projects and web development services, we couldn’t miss the opportunity to review the latest ACF security update. When collaborating with us, you can trust that we prioritize every aspect of your web project, including security. Please contact us if you need assistance enhancing your website’s functionality and security!
Contact

Send a Project Brief
You are currently viewing a placeholder content from Facebook. To access the actual content, click the button below. Please note that doing so will share data with third-party providers.
More InformationYou are currently viewing a placeholder content from Instagram. To access the actual content, click the button below. Please note that doing so will share data with third-party providers.
More InformationYou are currently viewing a placeholder content from X. To access the actual content, click the button below. Please note that doing so will share data with third-party providers.
More Information