Enterprise Application Architecture for Scalable Enterprise Websites
Table of Contents
Enterprise application architecture defines the foundational structure through which enterprise websites are designed, operated, and scaled. It functions as a layered system of separation and control that enables complex platforms to remain modular, cohesive, and adaptable at scale.
By enforcing architectural principles such as modularity, cohesion, scalability, security, and observability, it ensures that individual components remain independently manageable while the system as a whole maintains consistent behavior under changing demands.
As a specialized discipline within enterprise website architecture, this architecture governs how enterprise websites are developed, how systems are integrated across external platforms, and how different architectural models are selected to meet operational constraints. From release autonomy to component encapsulation, its influence spans deployment pipelines, scaling strategies, and integration protocols.
More than just structural scaffolding, enterprise application architecture enables development pipelines to evolve without fragmentation and supports organizational growth through coordinated, context-aware evolution.
What is Enterprise Application Architecture?
Enterprise application architecture is the structural framework that governs how an enterprise website is logically organized, behaviorally enforced, and operationally scaled. It defines a controlled system of separation — across interface rendering, logic execution, data management, and infrastructural support — that allows complexity to grow without compromising maintainability or performance.
This architecture establishes strict boundaries between services and layers, ensuring that each unit operates within a defined scope, with clear dependencies and predictable interactions. Modularity is enforced to isolate change, reduce coupling, and preserve autonomy across development teams. Observability and fault tolerance are embedded as system-wide behaviors, not post-development features, enabling real-time understanding and graceful degradation under load or failure.
By abstracting technical structure away from individual implementations, enterprise application architecture becomes the mechanism that supports scalable feature delivery, coordinated cross-team workflows, and sustained digital reliability. It does not merely shape how an enterprise website is built. It defines how it behaves, evolves, and integrates within the broader system landscape.
Architecture Layers of Enterprise Websites
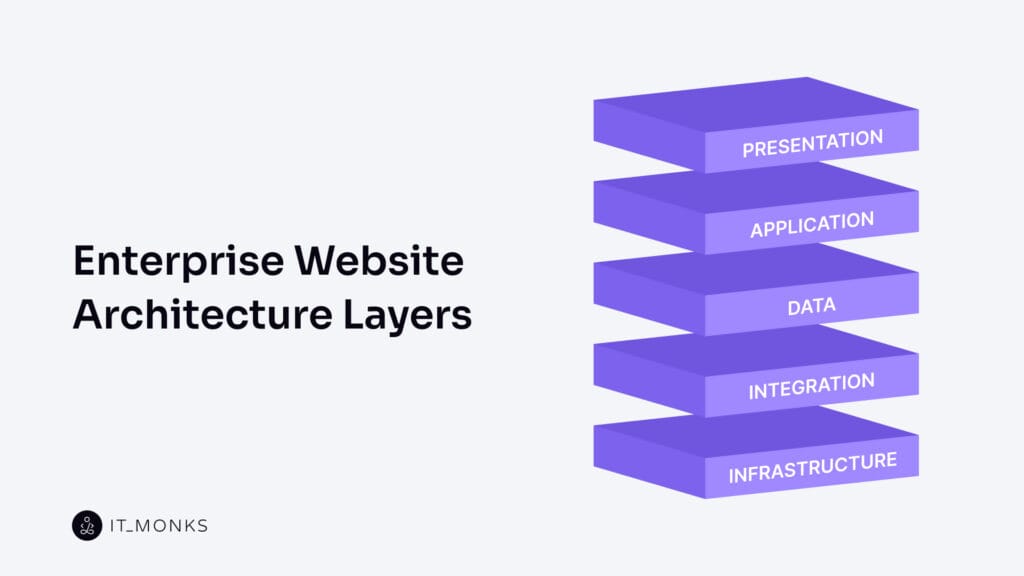
Enterprise application architecture enforces a layered structure within enterprise websites — one that governs the separation of interface rendering, logic orchestration, data control, system integration, and infrastructure execution.
These layers are not isolated modules but bounded architectural contexts, each designed to abstract specific concerns, coordinate system behaviors, and maintain operational clarity under scale.
This layered framework enables modular development, supports team autonomy, and preserves consistency across evolving system demands.
By establishing clear dependency flows (from the external presentation surface to the internal execution substrate) it ensures that each layer functions as a controlled predicate host, enforcing boundaries, enabling orchestration, and upholding system resilience. The architecture structures their logic, constrains their complexity, and stabilizes their growth.
Presentation Layer
The presentation layer abstracts the user interface as a distinct surface, rendering visual outputs received from the application layer without embedding any business logic or data operations. It exposes a contract to the user, delivering structured views and interaction flows while remaining fully decoupled from underlying services and persistence mechanisms.
By isolating interface responsibilities, the presentation layer enables performance tuning through SSR or CSR strategies, maintains predictable loading behavior, and allows for independent evolution of front-end experiences. It ensures that visual delivery remains flexible and scalable, without compromising the system’s architectural boundaries.
Application Layer
The application layer governs the orchestration of business logic across the enterprise website. It abstracts internal flows, enforces conditional execution paths, and manages how user intent is translated into system behavior. Acting as the core interpreter between interface inputs and backend processes, it defines the rules, dependencies, and control structures that drive functional outcomes.
This layer does not serve as middleware. It is the domain-specific logic hub that enables modular functionality, enforces API contracts, and ensures that operations remain consistent, traceable, and aligned with business context.
By isolating logic execution, the application layer supports scalable development and coordinated system behavior without entangling interface rendering or data persistence.
Data Layer
The data layer governs the definition, access, and persistence of structured state within the enterprise website. It abstracts data storage and retrieval operations, providing a clear boundary between business logic and underlying state management. As the authoritative source of truth, it ensures that all system behaviors rely on consistent, validated, and version-controlled data.
This layer enables flexible modeling to support distributed architectures, allowing application logic to interact with stored and cached data through well-defined interfaces.
By isolating data concerns, the data layer maintains integrity across transactions, supports scalability, and reinforces architectural separation between logic execution and state representation.
Integration Layer
The integration layer governs all interactions between the enterprise website and external systems through clearly defined architectural contracts. It abstracts communication protocols, mediates data exchange, and enforces isolation between internal logic and third-party dependencies such as CRMs, ERPs, IAMs, and analytics platforms.
By encapsulating integration logic, the integration layer protects the core architecture from vendor-specific behavior, brittle dependencies, and direct service coupling. It ensures that external systems interact through controlled interfaces, enabling fault-tolerant communication and maintaining the internal system’s modular integrity.
Infrastructure Layer
The infrastructure layer governs the execution environment that powers the enterprise website, abstracting compute, storage, and network resources into manageable and scalable units. It provides the substrate upon which all other architectural layers operate, whether deployed through containers, virtual platforms, or cloud-native services.
By decoupling physical resources from application logic, the infrastructure layer enables seamless scaling, high availability, and deployment flexibility across environments. It ensures that system resilience and performance can be maintained without requiring changes to the logic or behavior of upper layers, preserving the architectural integrity of the enterprise website under growth or operational shifts.
Principles of Enterprise Application Architecture
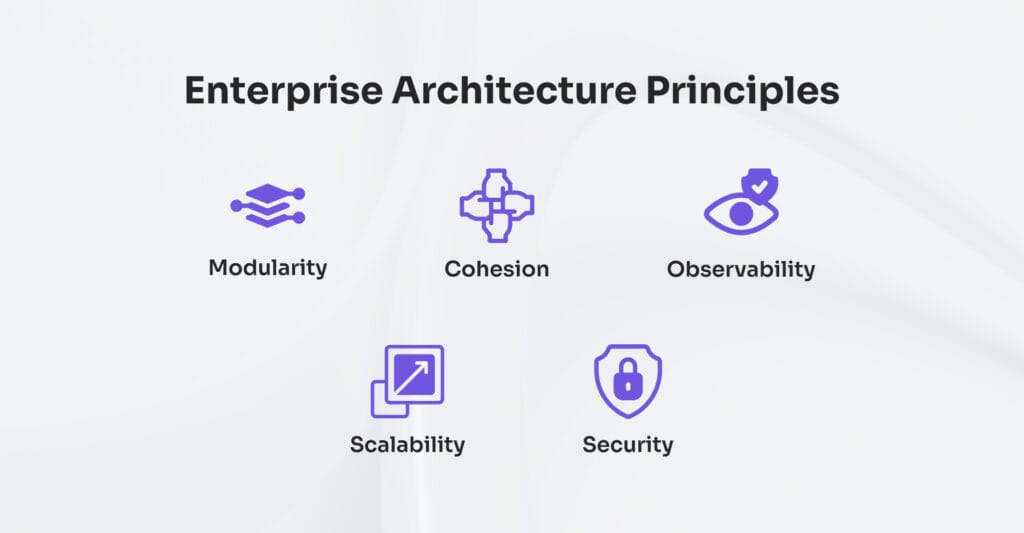
Enterprise application architecture governs the behavior and integrity of enterprise websites through five core system principles: modularity, cohesion, scalability, security, and observability.
Each principle enables specific structural control and functional enforcement:
- Modularity governs how components remain self-contained and interchangeable, allowing for easy replacement and integration.
- Cohesion preserves alignment within bounded contexts, minimizing internal fragmentation.
- Scalability supports predictable growth without architectural disruption.
- Security enforces trust boundaries and system-level access discipline.
- Observability maintains transparency by exposing operational signals for continuous insight.
Modularity
Modularity enables the architecture to isolate services and functions into distinct, self-contained units that operate independently of one another. It governs how responsibilities are distributed across the system, ensuring that each module can be developed, deployed, and replaced without impacting others.
This separation enforces strict control over scope and lifecycle, allowing updates to occur in isolation. Interface contracts between modules define clear interaction rules, preventing unintended dependencies and preserving system integrity as complexity grows.
Cohesion
Cohesion maintains internal consistency by aligning all logic and responsibilities within a defined architectural boundary. It ensures that each layer or module serves a singular, unified purpose, reducing noise and minimizing the risk of fragmented behavior.
By keeping functionality tightly bound, cohesion supports clear ownership and simplifies reasoning about system behavior. It prevents cross-cutting concerns from bleeding into unrelated areas, making the architecture more stable, predictable, and easier to evolve.
Scalability
Scalability enables the architecture to handle increased demand without compromising stability or performance. It preserves system integrity under load by supporting both vertical expansion of individual components and horizontal distribution across multiple instances.
This principle maintains clear separation between layers, so that scaling one part of the system does not require structural adjustments to others. By localizing the impact of growth, scalability ensures predictable behavior, efficient resource allocation, and operational continuity across evolving usage patterns.
Security
Security enforces access boundaries and trust zones across the architecture, ensuring that each layer and component operates within clearly defined limits. It governs how identity, permissions, and communication flows are controlled, preventing unauthorized interactions and isolating potential faults.
By embedding protective mechanisms into the structural design security preserves data integrity, limits exposure, and supports safe interaction across internal and external interfaces. This containment ensures that a compromise in one area does not propagate risk across the system.
Observability
Observability enables the architecture to expose its internal state through measurable signals that reflect system behavior. It governs how events, dependencies, and performance patterns are surfaced in real time, making the system intelligible from the outside in.
Signals such as logs, traces, and metrics are not afterthoughts; they are built into the structure to support accurate interpretation of flow and fault conditions. This continuous visibility allows for effective debugging, operational clarity, and faster resolution across distributed components.
Architecture in Enterprise Website Development
Enterprise website development is governed by the structural behaviors defined at the architecture level. Modularity, cohesion, scalability, security, and observability extend directly into how components are managed, releases are executed, development is organized, and failures are contained.
The enterprise website becomes the object shaped by these conditions. The architecture controls the rules of assembly, the pathways for change, and the mechanisms through which complexity is handled during build, deployment, and runtime. Each development function inherits its structure, constraints, and operational logic from the architecture that frames it.
Component Management
Component management is the architectural strategy that controls how reusable units are defined, versioned, and distributed within the enterprise website. Rooted in modularity and cohesion, it encapsulates functionality into isolated, self-contained blocks that operate within clearly scoped boundaries.
This structural approach enables safe updates, controlled dependencies, and predictable behavior across teams and services. By enforcing encapsulation and interface contracts, the architecture supports scalable collaboration while minimizing integration risk and change-related disruptions.
Release Pipeline
The release pipeline reflects how the architecture structures and controls the deployment lifecycle. It defines the order, conditions, and boundaries under which code moves from development to production, maintaining system integrity throughout.
Anchored in observability and layer separation, the release process is governed not by tooling but by architectural enforcement, ensuring that changes remain isolated, traceable, and recoverable. This enables fault containment, supports rollback strategies, and sustains overall system stability during continuous iteration.
Performance Scaling
Performance scaling describes the architectural behavior that enables runtime elasticity and development-time scalability. It is structured around decoupled services, abstracted infrastructure, and the ability to replicate system functions horizontally without introducing bottlenecks.
Through controlled distribution of load and isolation of performance domains, the architecture ensures that scaling one part of the system does not destabilize others. This supports continuous availability, efficient resource use, and responsive user experiences under varying demand.
Failure Recovery
Failure recovery is an embedded architectural mechanism that maintains system continuity in the event of faults. It relies on modular boundaries, observability signals, and abstracted infrastructure to isolate failure domains and trigger graceful degradation or self-healing behavior.
Rather than treating recovery as an external process, the architecture integrates it into the system’s operational logic, ensuring that faults remain contained, services remain responsive, and enterprise websites continue to function even under adverse conditions.
Architecture Models in Enterprise Systems
Enterprise application architecture manifests in multiple structural models, each shaped by the system demands and organizational constraints of enterprise website environments. These variants are not alternatives in competition, but contextual expressions of the same foundational framework, adapted to enforce different architectural priorities.
Each model reflects a shift in how modularity, cohesion, scalability, or other attributes are emphasized to meet specific operational needs. This plurality exists to align the architecture with real-world variations in scale, team autonomy, integration complexity, or performance goals.
By adjusting the balance of architectural behaviors, these models support flexible implementation paths while preserving the underlying mandate: governing system performance and development logic for scalable enterprise websites.
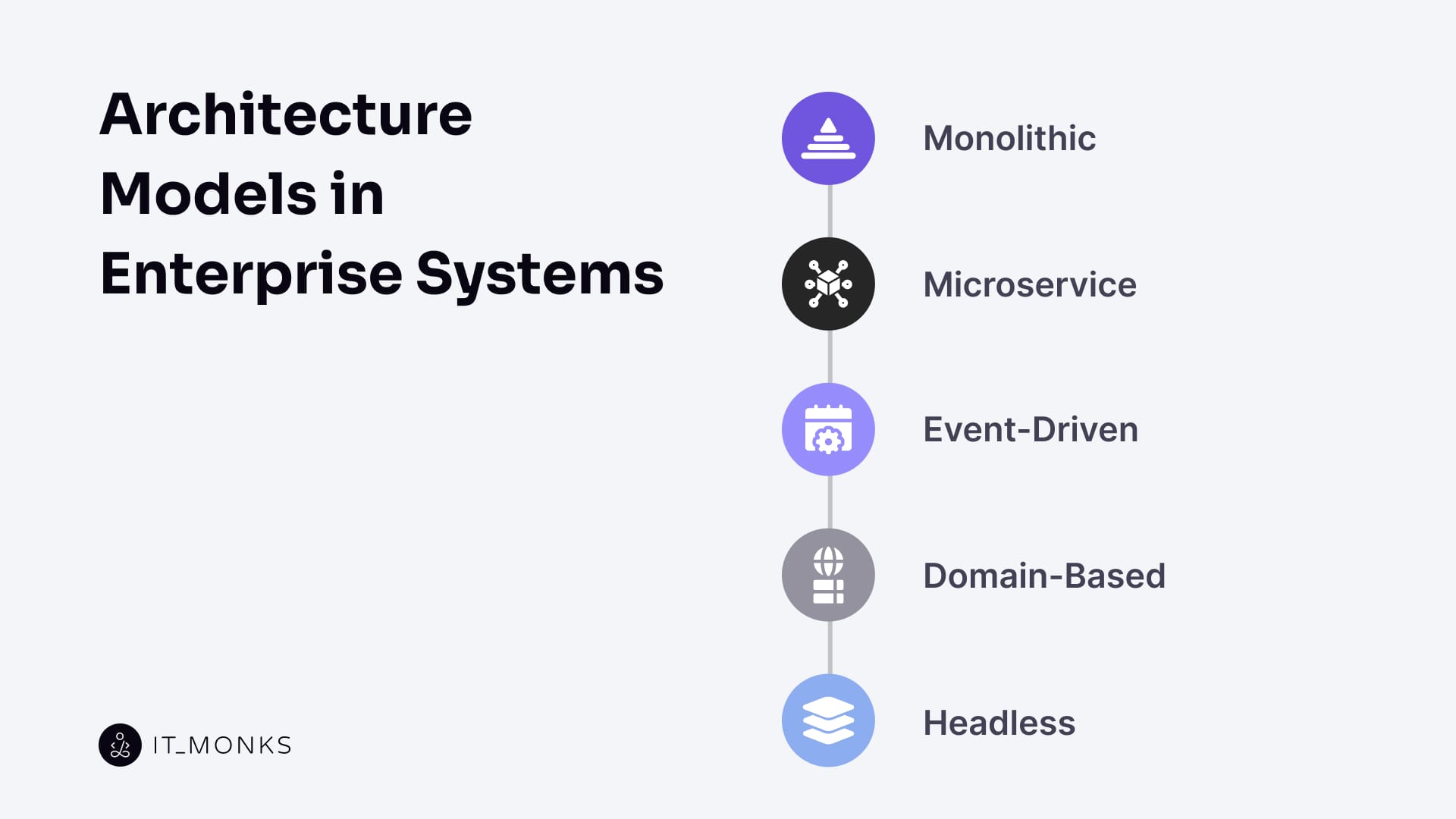
Monolithic Model
The monolithic model represents enterprise application architecture as a tightly integrated structure where interface, logic, and data layers are encapsulated within a single deployable unit. This model delivers all services in a unified scope, emphasizing internal cohesion and centralized control.
By aligning all functionality within a shared runtime, the monolithic architecture favors predictable control flow, clear internal dependencies, and minimal network overhead. Its simplicity enables faster initial development and deployment, particularly in environments with limited integration requirements or tightly scoped domains.
However, this configuration constrains modularity and scaling independence. Any change can impact the entire system, making it difficult to implement continuous delivery, horizontal scaling, and distributed team ownership at scale. As enterprise websites grow in complexity, the limitations of the monolithic model often surface in the form of deployment bottlenecks and reduced agility.
Microservice Model
The microservice model expresses enterprise application architecture as a distributed system composed of modular, independently deployable services. Each unit operates within its bounded context, with its own lifecycle, logic, and data scope.
This model prioritizes modularity, service decoupling, and release autonomy, enabling teams to build, deploy, and scale components in parallel without coordination bottlenecks. It supports granular scalability, resilient fault handling, and adaptive load distribution across the enterprise website infrastructure.
While the microservice model enhances development velocity and operational flexibility, it introduces architectural complexity. Communication between services requires strict contract governance, consistent interface definitions, and robust integration boundaries to preserve system integrity and avoid cascading failures.
Event-Driven Model
The event-driven model structures enterprise application architecture around asynchronous message propagation, where system components react to state changes through events rather than direct calls. Logic execution is decoupled from control flow, enabling components to operate independently while responding to system-wide triggers.
This model emphasizes decoupling, asynchronous coordination, and architectural observability. It supports flexible execution paths, promotes reactive workflows, and allows for soft failover by isolating failure domains through non-blocking communication.
In contrast to request-response models, which rely on tight, synchronous dependencies, the event-driven approach enables greater resilience and adaptability. However, it also demands robust telemetry pipelines to trace event flows, interpret system behavior, and maintain operational clarity as complexity increases.
Domain-Based Model
The domain-based model aligns enterprise application architecture with distinct business domains, structuring services around logically bounded contexts that reflect organizational functions and responsibilities. Each cluster of services is shaped by business logic, reinforcing semantic cohesion and domain-specific responsibility.
This model prioritizes internal alignment of responsibilities, separation of concerns, and team autonomy. By structuring the system according to domain boundaries, it improves cognitive alignment between development teams and business units, making ownership, accountability, and decision-making more direct and coherent.
Domain-based architecture inherits cohesion and supports modular growth, allowing enterprise websites to scale vertically within specific areas of functionality. It also reinforces clear team-level ownership, enabling parallel development across domains without cross-functional interference or dependency sprawl.
Headless Model
The headless model separates the presentation layer from the underlying service and application logic, allowing enterprise websites to deliver content and functionality across multiple channels without modifying core system behavior. UI rendering is abstracted from business processes, enabling front-end interfaces to evolve independently.
This architecture emphasizes decoupling, flexibility, and channel independence, supporting composable delivery across web, mobile, kiosk, and emerging interfaces. By enforcing a strict separation of concerns, the headless model leverages modularity of layers and integration-layer governance to maintain consistency while adapting to varied delivery contexts.
Headless architecture transforms the enterprise website into an interface-agnostic platform, capable of supporting multi-device experiences without duplicating logic or compromising system integrity.
System Integrations in Website Architecture
Enterprise application architecture governs system integrations in website architecture through defined, contract-based interfaces that manage how the enterprise website interacts with external systems.
Rather than allowing direct dependencies, the architecture abstracts, mediates, and encapsulates third-party logic to maintain structural integrity and modular isolation. In this context, integration is an architectural behavior that enforces clear boundaries while enabling operational coordination.
These integrations — whether with CRMs, ERPs, CDPs, or IAM platforms — are routed through the integration layer, which exposes only what is necessary and shields the core architecture from direct coupling. This ensures that all external communication remains isolated, observable, and governed by structural rules such as contract enforcement, idempotency, and retry control.
By treating integrations as risk-controlled dependencies, enterprise application architecture maintains system modularity and cohesion while enabling functional interoperability across the enterprise ecosystem. Each interface operates within a bounded boundary, ensuring that no external system compromises the behavior, security, or scalability of the enterprise website.
CRM Integration
CRM integration refers to a contract-bound architectural interface between the enterprise website and external Customer Relationship Management (CRM) systems. It operates entirely through the integration layer, which abstracts data flow, enforces boundary isolation, and mediates all bidirectional communication under strict architectural constraints.
The CRM is treated as a functional extension, not a core dependency. As such, CRM integration is version-controlled, dependency-isolated, and monitored to ensure system behavior remains predictable.
The architecture prevents direct service-to-service coupling, preserving modularity, security, and observability across layers. This separation ensures that internal business logic remains untouched by CRM-specific behavior, while still enabling controlled synchronization where required.
ERP Integration
ERP integration serves as a deep architectural boundary, facilitating interaction between the enterprise website and an external enterprise resource system. The architecture mediates this relationship through encapsulated interfaces (typically exposed via gateways or service layers), ensuring that the ERP remains an external authority, not a co-processor within the internal system.
Business logic within the enterprise website is kept strictly separate from ERP logic, with domain responsibilities clearly defined and divided. All data flows and protocol mappings are routed through the integration layer, protecting core layers from shared state assumptions or procedural entanglement.
CDP Integration
CDP integration establishes a structural interface between the enterprise website and external customer data platforms, enforcing modular interaction while maintaining system autonomy. The architecture controls this integration to ensure that internal logic remains insulated from external data aggregation behaviors.
All data exchange is governed by architectural contracts that preserve boundary clarity, enforce data governance policies, and prevent inversion of control. CDP integration is treated as a constrained dependency, one that operates within isolated contexts, inherits observability, and aligns with the system’s modular structure without introducing external logic into core layers.
IAM Integration
IAM integration enforces identity management and access governance within the enterprise website through a defined architectural boundary. Identity and permission logic are never embedded directly into the application layer; instead, they are delegated to an external authority system via controlled integration.
This integration supports access scoping, authentication delegation, and least-privilege enforcement, mediated through failure-tolerant mechanisms that preserve architectural separation.
IAM integration defines a clear perimeter for identity dependency exposure, ensuring that authentication flows are observable, recoverable, and insulated from the internal logic of the enterprise website.
Enterprise Application Architecture as a Business Enabler
Enterprise architecture enables domain-level modular growth by structuring how technical decisions map to evolving business requirements. It governs the conditions under which enterprise websites can scale, adapt, and segment functionality, without introducing instability or cross-system dependency risks.
This structure supports organizational change by by containing business logic. Through modular composition and boundary-aware design, architecture abstracts dynamic behaviors into self-contained domains. It maintains separation between internal workflows and platform infrastructure, enabling non-invasive adaptation across teams and services.
Enterprise application architecture is vital for any enterprise web development service. It ensures that new functionality — whether operational or customer-facing — can be integrated without violating architectural intent. Modularity allows services to evolve in isolation. Interface isolation protects internal logic from integration pressure. Observability ensures that every action remains visible and accountable across the stack.
Instead of enabling business outcomes directly, enterprise architecture preserves the coherence that makes outcomes achievable, by enforcing the structural conditions under which large-scale systems can evolve safely, predictably, and without deadlock.
Contact
Don't like forms?
Shoot us an email at [email protected]




