What is Enterprise Network Security?
Table of Contents

Enterprise network security is a comprehensive framework of measures designed to protect an organization’s network infrastructure, devices, data, and digital assets from unauthorized access, misuse, and damage.
The core goals are confidentiality (restricting access to authorized users only), integrity (preventing unauthorized data changes), and availability (ensuring reliable access to systems and data).
Enterprise network security integrates infrastructure protection, traffic control, data encryption, access management, and system availability. These measures are applied across all OSI model layers — from securing physical connections (Layers 1–2) to protecting applications (Layer 7) — recognizing that threats can emerge at any level.
Networks are often segmented into smaller zones to strengthen defenses. This segmentation limits the spread of threats and simplifies security management. Additionally, identifying the network’s attack surface (potential points where attackers might gain access) is crucial for prioritizing security efforts.
Key network security tools and technologies such as firewalls, intrusion detection and prevention systems (IDPS), virtual private networks (VPNs), and network access control (NAC) work together to monitor, control, and protect network traffic and access.
Building a secure enterprise network also requires balancing cost, scalability, and resiliency to ensure long-term, sustainable protection that supports business continuity.
What are the Core Goals of Enterprise Network Security?
The core goals of enterprise network security are to maintain confidentiality, integrity, and availability.
- Confidentiality ensures that sensitive data is accessible only to authorized users. Techniques like encryption, user authentication, and access controls prevent unauthorized access to information.
- Integrity involves maintaining data accuracy and consistency. It ensures that information is not altered or tampered with during storage or transmission. Hashing, digital signatures, and version control systems help protect data integrity.
- Availability means that systems, applications, and data are accessible when needed. This is achieved through load balancing, redundancy, failover systems, and protection against denial-of-service (DoS) attacks.
Confidentiality: Protecting Sensitive Data
Confidentiality is a fundamental goal of enterprise network security, focused on protecting sensitive information from unauthorized access and disclosure and ensuring that only authorized individuals can view it. If unauthorized individuals gain access to confidential data, it can lead to data breaches, financial loss, reputational damage, and legal consequences.
To ensure confidentiality, organizations use several key methods:
- Encryption of Data. Data is encrypted both in transit and at rest using algorithms that convert it into unreadable formats, which can only be decrypted by authorized users with the correct keys.
- Access Control. Systems are configured to allow access only to users with the appropriate permissions. Role-based access control (RBAC) and multi-factor authentication (MFA) are commonly used to enforce this.
- Network Traffic Monitoring. Intrusion detection systems (IDS) and firewalls continuously monitor network activity to identify and block unauthorized access attempts or suspicious behavior in real time.
Integrity: Ensuring Data Accuracy and Consistency
Integrity is the process of ensuring data remains accurate and reliable by preventing unauthorized modification or tampering throughout its entire lifecycle, from creation to storage and transmission.
Integrity is critical for enterprise network security because corrupted or altered data can lead to incorrect decisions, system failures, and security vulnerabilities. Even small unauthorized changes can compromise operations or erode trust in the system.
To protect data integrity, organizations commonly use the following methods:
- Checksums. Simple algorithms that generate a value based on data content. Any change in the data results in a different checksum, flagging potential corruption.
- Hashes. Cryptographic hash functions (like SHA-256) create unique fingerprints of data. These are used to detect even the slightest changes in files or messages.
- Digital Signatures. These use encryption to verify the origin and integrity of data. If the data is altered in any way after signing, the signature becomes invalid.
Availability: Maintaining Network and Service Access
Availability is the principle of ensuring that network services, applications, and data are consistently accessible to authorized users without interruption. Achieving availability involves building network resiliency — the ability to continue operating despite disruptions caused by cyberattacks (such as DDoS), hardware failures, software issues, or natural disasters.
To support this, enterprises rely on foundational concepts like:
- Redundancy: Deploying multiple systems or components so that if one fails, others can take over without loss of service.
- Failovers: Automatically switching to a backup system when the primary one becomes unavailable.
- Disaster Recovery: Establishing clear plans and infrastructure for restoring operations and data quickly after a major incident.
What are Key Components and Technologies of Enterprise Network Security?
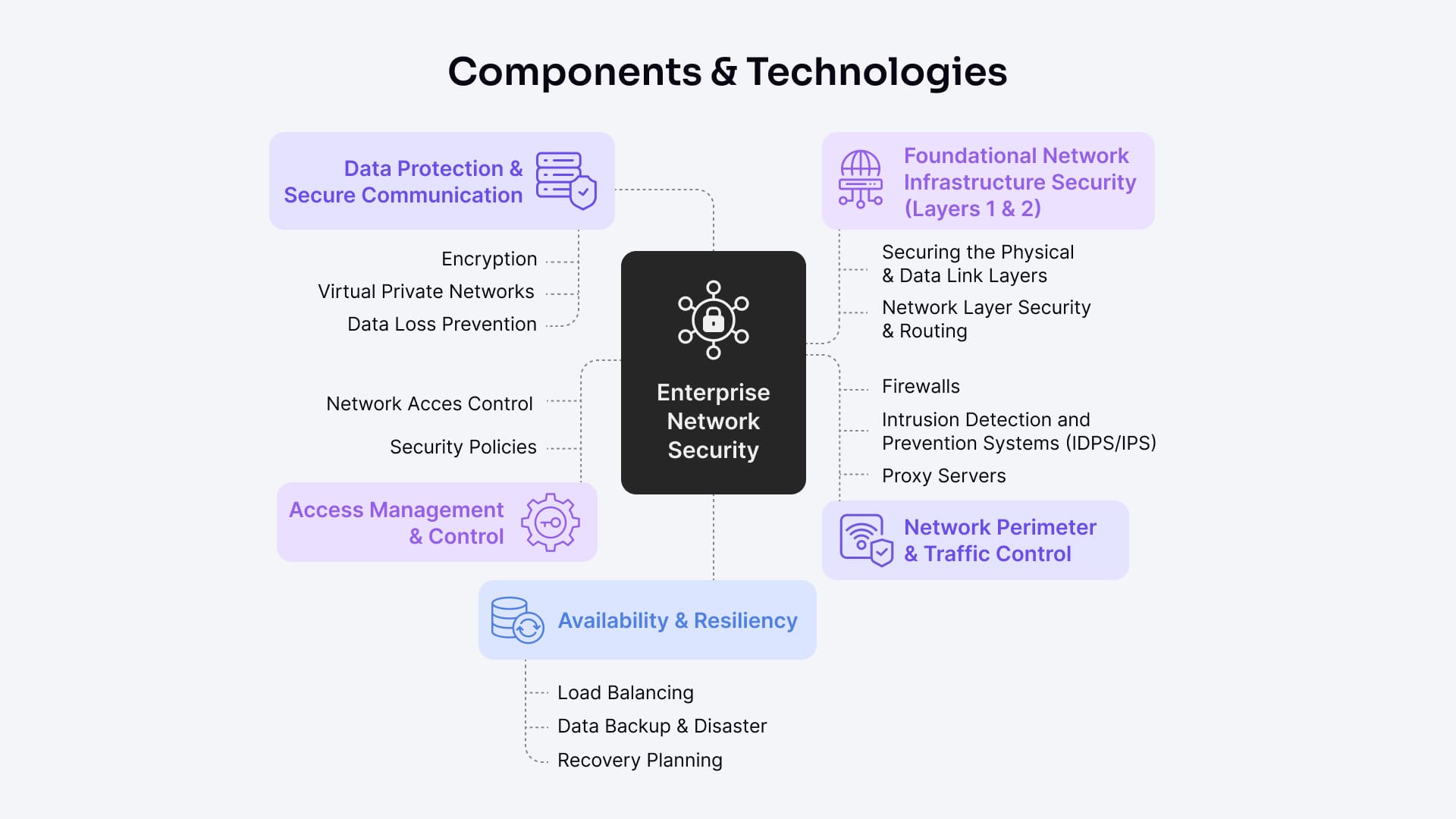
The key components and technologies of enterprise network security include infrastructure protection, traffic control, data security, access management, and ensuring system availability.
These cover securing the physical network layers and routing, controlling network perimeter traffic with firewalls and intrusion prevention, protecting data with encryption and VPNs, managing access through policies and network access control, and maintaining availability with load balancing and disaster recovery.
Foundational Network Infrastructure Security
Foundational network infrastructure security focuses on protecting the essential building blocks of an enterprise network, specifically the Physical Layer (Layer 1) and the Data Link Layer (Layer 2) of the OSI model.
These layers form the base of all communication. The goal is to prevent unauthorized physical access to network devices and to control how devices interact on the local network. If compromised, attackers can intercept traffic or disrupt operations before higher-level security measures even come into play.
To address these risks, key technologies and practices are applied at both layers. At Layer 1, this includes shielding and securing cables, monitoring for unauthorized device connections, and restricting physical access to hardware. At Layer 2, tools like MAC address filtering.
Securing the Physical and Data Link Layers (Layers 1 & 2)
Securing the Physical Layer (Layer 1) involves protecting the tangible components of the network infrastructure. This includes shielding network cables to prevent electromagnetic eavesdropping, implementing physical locks on network cabinets and server rooms, and using monitoring tools to detect unauthorized devices attempting to connect to the network.
At the Data Link Layer (Layer 2), security is focused on how devices communicate within the same local network. Key technologies include:
- MAC Address Filtering, which restricts access to only approved devices based on their hardware addresses.
- Virtual LANs (VLANs), which logically segment the network into isolated zones to limit broadcast domains and contain potential threats.
- Spanning Tree Protocol (STP), which ensures loop-free topologies and maintains network stability by dynamically disabling redundant paths.
Network Layer Security and Routing (Layer 3)
Layer 3 security focuses on protecting the routing and logical segmentation of network traffic. This layer manages IP addressing, enabling the separation of network segments and control over how data flows between them. Proper segmentation reduces the attack surface and helps contain potential breaches.
A key tool at this layer is the Access Control List (ACL). ACLs are used on routers, Layer 3 switches, and firewalls to filter traffic based on conditions such as source and destination IP addresses, port numbers, and protocols. They allow administrators to define which traffic is permitted or denied between segments.
IPsec (Internet Protocol Security) adds another layer of protection by authenticating and encrypting IP packets, ensuring data confidentiality and integrity across insecure networks like the internet.
Network Address Translation (NAT) is also commonly used at Layer 3. It masks internal IP addresses by translating them to public-facing ones, helping to obscure the internal structure of the network from external observers.
Security Zoning helps enforce different levels of trust within the network. Zones are created based on specific security requirements and can be implemented using VLANs, physical separation, or filtering devices.
Common zones include the Demilitarized Zone (DMZ) for public-facing services, Data Center Zones for critical infrastructure, User Zones for end-user access, and Management Zones for administrative control. This zoning approach limits access and exposure, making it easier to apply targeted security policies.
Network Perimeter and Traffic Control
Network perimeter and traffic control focuses on regulating how data enters and exits an enterprise network. This component is essential for preventing unauthorized access, inspecting traffic for threats, and enforcing security policies at the edge of the network.
These perimeter defenses act as the first line of protection between internal assets and external networks, such as the internet. By filtering, monitoring, and managing data flows, they reduce the risk of external attacks and help isolate compromised segments if a breach occurs.
Key technologies for perimeter and traffic control include firewalls (packet-filtering, stateful inspection, Next-Generation Firewalls, and Web Application Firewalls) for filtering and segmenting traffic, Intrusion Detection and Prevention Systems (IDPS) for monitoring and blocking malicious activity using signatures and behavioral analysis, and proxy servers (forward, reverse, and transparent) for managing access, inspecting content, and enhancing privacy between clients and external systems.
Firewalls: Filtering Network Traffic
Firewalls control and filter network traffic at the perimeter, allowing or blocking data based on defined security rules. They also help segment networks to contain threats and enforce policy boundaries.
There are several types of firewalls used in enterprise environments:
- Packet-filtering firewalls are the most basic type, inspecting traffic based on IP addresses, ports, and protocols. They operate at the network layer and make decisions without context of the connection state.
- Stateful inspection firewalls go further by tracking the state of active connections and evaluating packets in the context of the session. This provides a more intelligent and secure way to filter traffic.
- Next-Generation Firewalls (NGFWs) build on these capabilities by integrating advanced features like intrusion prevention, application-level inspection, user identity awareness, and cloud-delivered threat intelligence. Many NGFWs support modular feature licensing and cloud integration.
- Web Application Firewalls (WAFs) are specialized firewalls designed to protect web applications. They inspect HTTP traffic for malicious inputs and application-layer attacks, helping to defend against threats like SQL injection, cross-site scripting (XSS), and other common vulnerabilities.
Intrusion Detection and Prevention Systems (IDPS/IPS)
Intrusion Detection and Prevention Systems (IDPS/IPS) play a crucial role in protecting enterprise networks by identifying and responding to malicious activity. These systems monitor network traffic for suspicious behavior and act based on their type and configuration.
- Intrusion Detection Systems (IDS) are passive tools that analyze traffic and generate alerts when they detect potentially harmful activity. They log incidents and notify administrators but do not take direct action to block the threat. IDS is ideal for environments where a human analyst is available to evaluate alerts and determine the appropriate response.
- Intrusion Prevention Systems (IPS), on the other hand, take a more active role. In addition to detecting threats, IPS can automatically block or disrupt malicious traffic in real-time. This includes actions like dropping harmful packets, resetting connections, or reconfiguring firewalls to prevent further intrusion attempts.
Both IDS and IPS rely on a variety of detection techniques. These include signature-based detection (matching known threat patterns), heuristic analysis (evaluating behavior against expected norms), anomaly detection (flagging deviations from established baselines), and increasingly, machine learning and deep learning models that can identify new and evolving threats based on learned behaviors.
By combining these approaches, IDPS solutions can effectively identify and reduce the impact of cyberattacks before they cause damage, making them vital components in an enterprise network security strategy.
Proxy Servers: Controlling Access and Content
Proxy servers act as intermediaries between clients and the internet, handling requests on behalf of users. When a client attempts to access a website or online resource, the request is first sent to the proxy server, which then forwards the request to the destination and returns the response back to the client. This indirect access provides several benefits in enterprise network environments.
Proxies help control traffic flow, enforce access policies, and inspect content for security threats. For example, they can scan web content for malware or block access to non-compliant or harmful websites, ensuring that only safe and approved data reaches users.
Additionally, proxies can mask the IP addresses of internal clients, adding a layer of anonymity and helping to protect against targeted attacks.
There are several types of proxy servers used in enterprise settings:
- Forward proxies are positioned in front of client devices, typically managing and filtering outbound traffic to the internet. They’re useful for enforcing browsing policies or caching frequently accessed content to improve performance.
- Reverse proxies sit in front of web servers and manage incoming traffic from external users. They enhance security by shielding internal servers from direct exposure and can also balance load among multiple backend servers.
- Transparent proxies intercept traffic without requiring any configuration on the client side. They’re often used in environments where administrators want to implement proxy functionality without altering device settings.
Data Protection and Secure Communication
Data protection and secure communication are critical to maintaining the confidentiality and integrity of information across enterprise networks. This component focuses on safeguarding sensitive data both at rest and in transit, ensuring it cannot be intercepted, read, or leaked by unauthorized parties.
The goal is to prevent data breaches, unauthorized access, and data loss, especially as organizations increasingly operate across remote networks and cloud environments. Protecting communication channels and controlling the flow of information helps maintain trust, comply with regulations, and minimize business risk.
To achieve this, key technologies such as encryption (WPA2, SSL/TLS, IPsec), Virtual Private Networks (VPNs) for secure remote and site-to-site access, and Data Loss Prevention (DLP) systems for monitoring and blocking unauthorized data transfers are implemented to protect sensitive information and maintain secure communication.
Encryption Techniques for Data Security
Encryption is a fundamental technique for protecting data confidentiality. It transforms readable information into an unreadable format that can only be deciphered with the correct decryption key. This ensures that even if data is intercepted, it remains useless to unauthorized parties.
Encryption is used extensively in enterprise environments to protect data both at rest and in transit. For example, WPA2 is widely used to secure wireless networks by encrypting data transmitted over Wi-Fi. SSL/TLS protocols, such as login credentials and payment details, safeguard information sent between web browsers and servers. At the network layer, IPsec encrypts IP packets to provide secure communication between devices.
Virtual Private Networks (VPNs) also rely on encryption to create secure, encrypted tunnels for data to travel through untrusted networks like the internet. By applying these encryption methods, organizations can maintain the privacy and integrity of their communications and protect sensitive data from being exposed during transmission.
Virtual Private Networks (VPNs) for Secure Remote Access
Virtual Private Networks (VPNs) establish a secure, encrypted connection, often called a “tunnel”) between a user or device and a trusted network over the public internet. This protects data in transit from interception, ensuring that sensitive information remains private and secure even when transmitted through untrusted networks.
VPNs are used to safeguard internet connections by masking users’ IP addresses and encrypting the data they send and receive. This helps preserve user privacy and prevents unauthorized access to corporate systems.
There are two primary types of VPNs:
- Remote access VPNs, which allow individual users to connect to an organization’s network from any location securely
- Site-to-site VPNs, which link entire networks (such as a company’s branch offices) to each other over a secure tunnel
Data Loss Prevention (DLP)
Data Loss Prevention (DLP) is a security approach focused on identifying, monitoring, and controlling the movement of sensitive data to prevent unauthorized access, transfers, or leaks. Its primary goal is to ensure that confidential or critical information (such as personal data, intellectual property, or financial records) does not leave the organization unapproved or insecure.
DLP systems work by analyzing data in use (on endpoints), in motion (moving through the network), and at rest (stored on devices or servers). They apply predefined rules or policies to detect and block actions that could result in data loss, such as copying files to USB drives, sending confidential attachments via email, or uploading sensitive documents to cloud services.
Access Management and Control
Access Management and Control is a component of enterprise network security that ensures only authorized users and devices can access network resources, protecting against unauthorized access and potential breaches. It controls how users and devices connect, maintaining the integrity and confidentiality of the network.
Key technologies include Network Access Control (NAC), which manages network entry by disabling unused switch ports, filtering or limiting MAC addresses, and enforcing authentication protocols such as IEEE 802.1X using EAP, RADIUS, or TACACS+.
Network Access Control (NAC)
Network Access Control (NAC) is a security framework that manages how users and devices connect to a network, ensuring that only authorized and compliant endpoints are granted access. It enforces policies at the point of entry, which helps organizations maintain control over who and what can interact with their internal resources.
One of the simplest NAC techniques is physically disabling unused ports on network switches to eliminate unnecessary access points. Another common method is filtering or limiting connections based on MAC addresses, allowing only approved devices to connect.
For more dynamic and scalable control, NAC solutions often use authentication protocols like IEEE 802.1X, which verifies user and device identities before permitting access.
This process typically involves communication with authentication servers using protocols such as EAP (Extensible Authentication Protocol), RADIUS (Remote Authentication Dial-In User Service), or TACACS+ (Terminal Access Controller Access-Control System Plus).
Implementing Robust Security Policies
A comprehensive security policy is the foundation of an organization’s cybersecurity framework. It establishes clear rules and expectations for how users interact with technology resources, how devices are managed, and how the organization responds to security incidents.
These policies guide user behavior by defining acceptable use, password management, and access controls, reducing the risk of accidental breaches or insider threats. They also set standards for device management, including guidelines for patching, antivirus use, and secure configuration, ensuring all systems are maintained in a secure state.
Just as critically, a well-defined incident response plan within the policy outlines procedures for identifying, reporting, and responding to security events. This helps contain threats quickly, minimize damage, and ensure business continuity. By setting these standards across all operational levels, robust security policies create a structured approach to managing risk and protecting the organization’s digital environment.
Ensuring Availability and Resiliency
Ensuring availability and resiliency is a fundamental aspect of network security that focuses on keeping systems up and running smoothly, even in the face of failures or attacks.
Downtime or service interruptions can lead to significant financial losses, reputation damage, and critical business operations disruption. The goal is to maintain consistent access to network resources and services, ensuring that users and applications can operate without interruption.
Key technologies that support availability and resiliency include load balancing, which distributes incoming requests evenly across multiple servers to prevent overload and improve performance while mitigating Denial of Service (DoS) attacks, and regular data backups combined with disaster recovery (DR) planning, which ensures that critical functions can be quickly restored after disruptions, minimizing downtime and maintaining business continuity.
Load Balancing for Performance and Availability
Load balancers are essential components in modern enterprise networks. They act as intermediaries that intelligently distribute incoming traffic across multiple servers. Rather than allowing a single server to handle all user requests, which could lead to slowdowns or failures, load balancers ensure that traffic is evenly spread, optimizing the use of resources and maintaining smooth performance even under heavy demand.
By directing each user request to the most appropriate and available server, load balancers help reduce server overload, improve response times, and enhance the overall reliability of web applications and services. This balanced approach enhances user experience and plays a key role in defending against Denial of Service (DoS) attacks. When an attacker tries to flood the network with requests, a well-configured load balancer can absorb and distribute the traffic, preventing any single server from becoming a point of failure.
Load balancers also add a layer of redundancy and fault tolerance. If one server goes down, the load balancer seamlessly reroutes traffic to functioning servers, maintaining service continuity without user disruption.
Data Backup and Disaster Recovery Planning
Regular data backups are a fundamental part of enterprise network security, safeguarding against hardware failures, software corruption, cyberattacks, and human errors. Since no system is immune to failure, creating secure, consistent backups ensures critical data can be restored quickly, minimizing downtime and data loss.
A Disaster Recovery (DR) plan complements backup practices by outlining the procedures and resources required to restore IT systems and business operations after a disruptive event. This includes predefined steps for recovering data, reestablishing network access, and restoring essential services. A well-crafted DR plan prioritizes critical functions, defines recovery time objectives (RTOs) and recovery point objectives (RPOs), and assigns responsibilities to specific teams.
Strategies for Implementing Enterprise Network Security

Implementing enterprise network security involves strategies such as layered defenses, continuous monitoring, regular updates and patching, Zero Trust access controls, and a clear understanding of the attack surface to reduce vulnerabilities.
Defense-in-Depth Strategy
The defense-in-depth strategy is like having several lines of defense stacked together to protect a network. Instead of relying on just one security measure, it uses multiple layers that cover different aspects:
- Physical security protects the hardware itself, like locking server rooms or securing network cables to prevent unauthorized physical access.
- Technical security includes firewalls, encryption, antivirus software, and access controls that defend the network and data from cyberattacks.
- Administrative security involves policies, procedures, training, and monitoring to make sure people follow security best practices and respond properly to threats.
Combining these layers ensures that if one layer fails or is bypassed, the other layers still stand guard, making it much harder for attackers to breach the entire system.
Continuous Monitoring and Auditing
By continuously observing network traffic and user activity, organizations can spot unusual patterns or behaviors that may signal an attempted breach or internal misuse.
Tools like Security Information and Event Management (SIEM) systems aggregate and analyze logs from various sources in real time, allowing security teams to detect threats faster and respond more effectively.
Beyond real-time monitoring, regular security audits play a vital role in reviewing the overall security posture. They help identify outdated configurations, overlooked vulnerabilities, or gaps in policy enforcement.
Regular Updates and Patching
Reviewing security policies regularly, auditing current strategies, and implementing necessary changes are critical steps to maintaining a resilient network.
Equally important is keeping all systems, devices, and firmware up to date and applying patches and updates addresses known vulnerabilities that attackers might exploit. Timely patching closes security gaps and ensures the organization is protected against newly discovered threats, helping maintain system integrity and overall security posture.
Adopting Zero Trust
The Zero Trust security model is built on the principle of “Never trust; always verify.” Unlike traditional perimeter-based defenses that assume internal users and devices are trustworthy, Zero Trust requires strict verification for every access request, regardless of whether the user or device is inside or outside the corporate network.
This model enforces continuous authentication and authorization, validating user identities, device health, and access permissions at every step. Zero Trust significantly reduces the risk of unauthorized access and lateral movement within the network by minimizing implicit trust and segmenting resources.
Understanding the Network Attack Surface
The network attack surface refers to all the points where an unauthorized user or attacker could potentially enter or extract data from a system. These entry points span across multiple layers of the network and include both hardware and software components.
- At Layer 1/2, this might involve physical access to cables, switches, or wireless signals.
- At Layer 3, attackers may exploit IP-level vulnerabilities, such as spoofing or misconfigured routing.
- At Layer 4 and above, threats include exploiting open ports, application flaws, insecure APIs, or poor authentication mechanisms.
Understanding these potential ingress points is essential for proactively identifying and minimizing vulnerabilities. By analyzing and managing the attack surface, organizations can prioritize their defenses and limit the opportunities for intrusion, helping to secure their networks more effectively.
Contact
Don't like forms?
Shoot us an email at [email protected]
Send a Project Brief
You need to load content from reCAPTCHA to submit the form. Please note that doing so will share data with third-party providers.
More InformationYou are currently viewing a placeholder content from Turnstile. To access the actual content, click the button below. Please note that doing so will share data with third-party providers.
More InformationYou are currently viewing a placeholder content from Facebook. To access the actual content, click the button below. Please note that doing so will share data with third-party providers.
More InformationYou are currently viewing a placeholder content from Instagram. To access the actual content, click the button below. Please note that doing so will share data with third-party providers.
More InformationYou are currently viewing a placeholder content from X. To access the actual content, click the button below. Please note that doing so will share data with third-party providers.
More Information



