WordPress Security [Complete Guide]
Table of Contents

WordPress is the most popular CMS worldwide, installed on over 43% of websites. The impressive demand makes it one of the most attacked content management systems and lucrative targets for hackers. Just imagine – there are over 90,000 attacks per minute on WordPress. Many websites are being hacked due to fake plugins. 84% of all security vulnerabilities on the web are the result of XSS attacks. However, many WordPress websites are hacked because of weak passwords. As you can see, your WordPress website can become a victim of multiple security risks. How to keep it safe? This comprehensive WordPress security guide discusses how not to become a victim of scammers and provides advanced WordPress security tips every website owner should follow.
Why Is WordPress Security Important?
Website security is crucial for safeguarding your business’s revenue and reputation. A compromised WordPress site can lead to unauthorized access, data theft, malware installation, and malicious software distribution to your users.
In March 2016, Google flagged over 50 million website users about potential malware or data theft risks. Additionally, Google blacklists approximately 20,000 websites for malware and around 50,000 for phishing every week.
Businesses with an online presence using WordPress as their platform of choice should prioritize their website security just like they would secure a physical store building. The owner’s responsible for protecting their business website from cyber threats like hacking attempts and data breaches.
How a Website Might Be Hacked
Websites can be hacked through various means, and understanding these vulnerabilities is crucial for maintaining online security. Here are some common methods hackers use to compromise websites:
- SQL Injection (SQLi). This is one of the most prevalent methods where attackers inject malicious SQL code into input fields or URLs, exploiting website code vulnerabilities. Hackers can then gain unauthorized access to the website’s database, retrieving sensitive information or modifying, deleting, or inserting new data.
- WordPress Cross-Site Scripting (XSS). XSS attacks involve injecting malicious scripts into web pages viewed by other users. These scripts can steal cookies, session tokens, or other sensitive information.
- Brute Force Attacks. In a brute force attack, hackers use automated tools to repeatedly guess usernames and passwords until they find the correct combination.
- File Inclusion Exploits. Hackers exploit vulnerabilities in web applications to include malicious files, such as PHP scripts, on the server. By executing these scripts, attackers can gain control over the server, access sensitive files, or compromise user data.
- Cross-Site Request Forgery (CSRF). CSRF attacks trick authenticated users into executing unwanted actions on a website where they are already logged in. This can lead to unauthorized transactions, data manipulation, or account takeover.
- Outdated Software and Plugins. Websites running outdated content management systems (CMS), plugins, or server software are more susceptible to attacks. Hackers exploit known vulnerabilities in these outdated versions to access the website.
- Denial of Service (DoS) and Distributed Denial of Service (DDoS). These attacks overwhelm a website’s server with traffic, rendering it inaccessible to legitimate users. Hackers may use botnets or other means to orchestrate these attacks, causing significant downtime and disruption.
- Social Engineering. Attackers may exploit human weaknesses rather than technical vulnerabilities. They might trick website administrators or users into revealing sensitive information or credentials through phishing emails, phone calls, or other means.
WordPress Security Tips
Ensuring the security of WordPress websites is crucial for protecting sensitive data and maintaining user trust. Below, we’ll outline some of the most important and common actions website owners can take to enhance their WordPress security.
WordPress Version
WordPress regularly releases software updates to enhance performance and security, safeguarding your site from cyber threats. Updating your WordPress version is a straightforward method to bolster its security. Surprisingly, approximately half of WordPress sites are using outdated versions, rendering them more susceptible.
To verify if you have the latest version of WordPress, simply log in to your admin area and go to WordPress Dashboard → Updates on the left menu panel. If it indicates that your version is not current, we strongly advise updating it promptly.
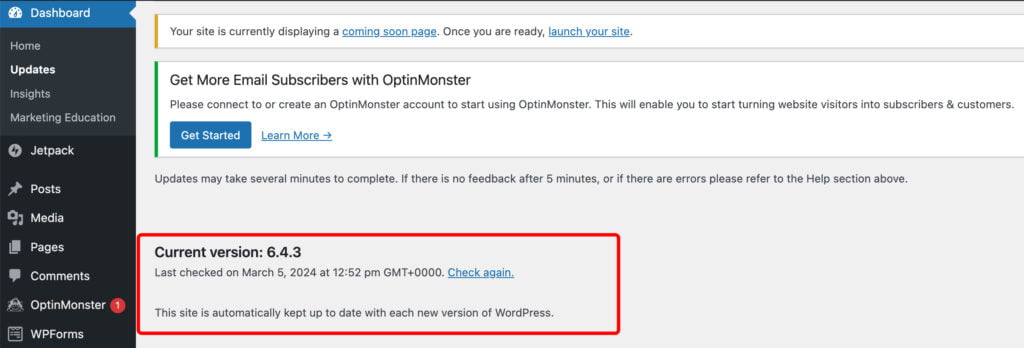
How to Update WordPress Version
Updating the WordPress versions is crucial for maintaining website security as it patches known vulnerabilities and strengthens defenses against potential exploits. To update WordPress, log in to your WordPress dashboard, navigate to the Updates section, and click on the “Update Now” button if a new version is available. Alternatively, automatic updates can be enabled for minor releases to ensure timely updates.
How to Hide WordPress Version
Hiding the WordPress version is important to prevent potential attackers from identifying vulnerabilities associated with specific versions. This adds an extra layer of security by obscuring information that could be used in targeted attacks. To hide the WordPress version, you can edit the theme’s functions.php file or use the best WordPress security plugins that offer features to hide or obfuscate the version information.
Here’s how to hide the WordPress version using a theme’s functions.php file:
- Access your WordPress dashboard.
- Navigate to “Appearance” > “Theme Editor.”
- Select the theme’s functions.php file from the list of theme files on the right.
- Add the following code snippet at the end of the functions.php file:
// Hide WordPress version from scripts and styles
function remove_wp_version_strings($src) {
global $wp_version;
parse_str(parse_url($src, PHP_URL_QUERY), $query);
if (!empty($query['ver']) && $query['ver'] === $wp_version) {
$src = remove_query_arg('ver', $src);
}
return $src;
}
add_filter('script_loader_src', 'remove_wp_version_strings');
add_filter('style_loader_src', 'remove_wp_version_strings');
// Remove generator tag
function remove_wp_version_tag() {
return '';
}
add_filter('the_generator', 'remove_wp_version_tag');Save the changes.
Suppose you prefer not to modify theme files directly. In that case, you can use a security plugin like “WP Hide & Security Enhancer” or “Hide My WP” to easily hide the WordPress version without coding. These plugins offer user-friendly interfaces where you can toggle various security settings, including hiding the WordPress version.
After implementing one of these methods, the WordPress version will no longer be visible in the page source code or any other publicly accessible area of your website, helping to improve its security posture.
WordPress Plugins and Theme
WordPress plugins and themes are intended to extend the functionality and design of WordPress websites. Plugins add new features or modify existing ones, while famous WordPress themes control the website’s visual appearance. While plugins and themes enhance the capabilities of WordPress sites, they also introduce potential security risks if not properly managed.
Plugins and themes play a significant role in website security because they can introduce vulnerabilities if they are outdated, poorly coded, or come from untrustworthy sources. Hackers often target vulnerable plugins and themes to exploit weaknesses, gain unauthorized access to websites, steal data, or inject malicious code.
Consider the following action tips to maintain website security regarding plugins and themes.
Use a Trusted WordPress Theme
Unauthorized versions of original premium themes, known as nulled WordPress themes, are often sold at a reduced price to attract users. However, they typically come with numerous security issues. Nulled theme providers are frequently hackers who have compromised the original premium theme by inserting malicious code such as malware and spam links. Additionally, these themes can serve as backdoors for other vulnerabilities that may jeopardize your WordPress site’s security.
Due to their illegal distribution, users of nulled themes do not receive any support from the developers. Consequently, if your site encounters any issues while using a nulled theme, you must troubleshoot and secure your WordPress site independently.
Selecting a WordPress theme from its official repository or reputable developers is advisable to avoid becoming a target for hackers’ activities associated with nulled themes. Alternatively, consider exploring third-party themes in official marketplaces, or opt for a better and the most reliable option – order custom WordPress development, and rest assured your website is one-of-a-kind and secure.
Use WordPress Security Plugins
Utilizing dedicated security plugins for WordPress offers an automated and efficient approach to strengthening your WordPress site’s security. Here’s a brief overview:
- Firewall Protection. Security plugins for WordPress are equipped with robust firewall protection, actively monitoring and filtering malicious traffic to prevent unauthorized access.
- Malware Scanning and Removal. These plugins conduct regular WordPress security scans, identifying and removing any malware or malicious code that may have infiltrated your WordPress installation.
- Login Protection. Features like two-factor authentication and login attempt monitoring secure the login process, protecting against brute force attacks.
- User Activity Monitoring. Security plugins track user activities, providing insights into suspicious behavior or unauthorized access.
- Regular Security Audits. Automated security audits help identify vulnerabilities and potential issues for prompt remediation.
Audit WordPress Theme and Security Plugins
Auditing WordPress themes and plugins is crucial for maintaining website security. Themes and plugins can introduce vulnerabilities, and regular audits help identify and address potential security risks. This ensures your website protects against malware injections, data breaches, and unauthorized access.
Regularly auditing WordPress themes and security plugins is recommended, ideally monthly or quarterly. Additionally, perform audits after major WordPress updates or whenever new security vulnerabilities are disclosed.
How to Do This
1. Review Installed Themes and Plugins
- Log in to your WordPress dashboard.
- Navigate to “Appearance” > “Themes” to view installed themes and “Plugins” > “Installed Plugins” to view installed plugins.
- Note down the names and versions of each theme and plugin.
2. Research Vulnerabilities and Updates
Check the WordPress.org repository, plugin/theme developer websites, or security advisories for any reported vulnerabilities related to your themes and plugins.
Verify if there are any available updates for the themes and plugins.
3. Conduct Security Scans
- Utilize security plugins like Wordfence, Sucuri Security, or iThemes Security to perform comprehensive security scans of your website.
- These scans will identify any known vulnerabilities, malware, or suspicious activity related to installed themes and plugins.
4. Implement Fixes and Updates
- If any vulnerabilities or issues are identified during the audit and scans, take immediate action to address them.
- Update outdated themes and plugins to the latest versions that include security patches.
- Remove or replace insecure themes or plugins with more secure alternatives if necessary.
Remove Unused WordPress Themes and Plugins
Removing unused WordPress themes and plugins is essential for reducing your website’s attack surface. Even if unused, themes and plugins can still pose security risks if they are outdated or vulnerable. Removing them minimizes the potential for exploitation and improves overall website security.
Regularly review and remove unused themes and plugins from your WordPress website. Perform this cleanup task quarterly or whenever new themes or plugins are installed or removed.
How to Do This
1. Identify Unused Themes and Plugins
- Access your WordPress dashboard.
- Navigate to “Appearance” > “Themes” and “Plugins” > “Installed Plugins” to list all installed themes and plugins.
- Determine which themes and plugins are not actively used on your website.
2. Deactivate and Delete Unused Themes and Plugins
- To deactivate a theme or plugin, click the “Deactivate” button next to its name.
- Once deactivated, click the “Delete” option to permanently remove the unused theme or plugin from your WordPress installation.
Note: Before deleting any theme or plugin, ensure that it is unused and not required for any essential functionality on your website.
Admin Page and Login Page
While it might sound obvious, paying attention to login credentials is super important as they serve as the first defense against unauthorized access to your WordPress website. According to WordPress.com, weak login credentials are one of the primary reasons for website hacks. Therefore, protecting your login page and using secure WP-admin login credentials are crucial for maintaining website security.
Use Secure WP-Admin Login Credentials
Statistics indicate that approximately 8% of WordPress sites fall victim to hacking due to weak or stolen passwords. This underscores the importance of employing strong, unique passwords for your WP-Admin login. Securing your WP-Admin login credentials is paramount for fortifying the security of your WordPress website.
Here’s why it matters:
- Preventing Unauthorized Access. Robust credentials are a barrier against unauthorized individuals attempting to gain entry into your website’s admin panel.
- Safeguarding Sensitive Data. Your website may house sensitive information, such as customer data, which could be compromised if your login details are not adequately secure.
- Preserving Reputation. A breach resulting from weak credentials can tarnish your site’s reputation and lead to a loss of trust among users.
- Averting Website Downtime. Successful hacks can cause downtime for your site, potentially resulting in revenue loss.
In addition to utilizing secure credentials, it is advisable to alter the default WordPress login URL, restrict login attempts as a preventive measure against brute force attacks; enable two-factor authentication; and incorporate captcha on the WordPress login page. Regularly updating WordPress core components, plugins, and themes is also vital in upholding website security.
Employing robust and distinctive passwords for accessing the admin section of WordPress is crucial in preventing unauthorized access and thwarting brute-force attacks. Weak passwords are susceptible targets for hackers and can lead to compromised websites and breaches involving data loss – ultimately causing you to lose control over your online presence.
How To Achieve This:
- Opt for lengthy, complex passwords encompassing letters, codes, special characters
- Steer clear from using common words, phrases, or quickly guessable information like birthdays or pet names
- Consider leveraging password management tools to generate store highly secure admin logins
- Frequently update refresh create new separate sets across multiple platforms accounts
Use Pre-login CAPTCHAs or Security Question
Pre-login CAPTCHAs or security questions are additional security measures added to the login page to verify the authenticity of users before granting access.
Pre-login CAPTCHAs or security questions help prevent automated bots and malicious scripts from brute-forcing login attempts. Requiring users to complete a CAPTCHA or answer a security question adds an extra layer of protection against unauthorized access.
How to Use It:
- Install a CAPTCHA plugin like Google reCAPTCHA or a security plugin offering CAPTCHA functionality.
- Configure the plugin settings to display a CAPTCHA challenge on the login page.
- Alternatively, you can set up security questions by using plugins or custom code to prompt users to answer predefined questions before logging in.
Enable Two-Factor Authentication
Two-factor authentication (2FA) adds an extra layer of security by requiring users to provide two forms of identification before accessing their accounts. Typically, this involves something they know (password) and have (e.g., a mobile device).
Two-factor authentication significantly enhances login security by making it more difficult for unauthorized users to gain access, even if they have obtained the password. It helps mitigate the risks associated with password theft, phishing attacks, and brute-force attempts.
How to Do This:
- Install a two-factor authentication plugin such as Google Authenticator, Authy, or Duo Security.
- Configure the plugin settings to enable two-factor authentication for WordPress logins.
- Users will be prompted to set up 2FA during the login process, typically by scanning a QR code or entering a code sent to their mobile device.
Limit Login Attempts
Login attempt limiting restricts the number of failed login attempts from a single IP address within a specified period.
Limiting login attempts helps prevent brute force attacks by blocking IP addresses that exceed the allowed number of failed login attempts. This reduces the likelihood of unauthorized access to the WordPress admin area.
How to Do This:
- Use a security plugin like Wordfence, iThemes Security, or Limit Login Attempts Reloaded.
- Configure the plugin settings to specify the maximum number of login attempts allowed before blocking the IP address.
- Set the duration for which an IP address is blocked after exceeding the login attempt limit.
Log Idle Users Out Automatically
Automatic logout functionality terminates user sessions after inactivity to prevent unauthorized access to logged-in accounts.
Automatic logout helps protect against session hijacking and unauthorized access to user accounts when devices are left unattended or shared. It reduces the risk of unauthorized access due to forgotten or unattended sessions.
How to Do This:
- Use a security plugin that offers automatic logout functionality or implement custom code to achieve this.
- Configure the plugin settings to specify the idle timeout duration after which users will be automatically logged out.
- Users will be logged out automatically if they remain inactive for the specified period.
Change the WordPress Login Page URL
Changing the WordPress login page URL involves modifying the default login URL (/wp-admin or /wp-login.php) to a custom URL of your choice.
Changing the login page URL adds an extra layer of obscurity and makes it more difficult for attackers to locate the login page. This helps protect against automated bots and brute force attacks targeting the default login URL.
How to Do This:
- Use a security plugin like WPS Hide Login or Rename wp-login.php.
- Install and activate the plugin, then navigate to its settings page.
- Enter the custom login URL you wish to use and save the changes.
- Users will now access the login page using the custom URL instead of the default WordPress login URLs.
.HTACCESS
The .htaccess file is a configuration file used by web servers, including Apache, to control and manipulate the processing of web requests. It allows users to override default server settings, set up redirects, block access to specific directories, and enhance website security. Below, we’ll outline the most common action users can take with this file to protect their WordPress website.
Protecting .htaccess
The .htaccess file allows users to set up rules and directives that affect how the server handles requests, including access control and URL rewriting.
Protecting the .htaccess file is crucial as it contains directives governing website security measures. Unauthorized access or tampering with this file can compromise website security and lead to vulnerabilities such as directory traversal attacks, unauthorized access to sensitive files, or server misconfigurations.
To protect the .htaccess file:
- Set the correct file permissions to restrict access. Use chmod or a similar command to set the permissions to 644, which allows read and write access for the owner and read-only access for others.
- Regularly monitor the file for unauthorized changes and restore from backups if necessary.
- Consider implementing additional security measures such as IP restrictions or web application firewalls to prevent unauthorized access to the server.
Securing wp-config.php
The wp-config.php file is a crucial WordPress configuration file that contains sensitive information such as database credentials, authentication keys, and other configuration settings. It is essential for the functioning of a WordPress site.
Securing the wp-config.php file is critical because compromising this file can lead to unauthorized access to the WordPress database containing sensitive user data. An attacker gaining access to this file could potentially take control of the entire WordPress site, leading to data breaches, defacement, or other malicious activities.
To secure the wp-config.php file:
- Move the wp-config.php file outside of the public_html or web root directory if possible. This prevents direct access to the file via the web browser.
- Set strict file permissions for the wp-config.php file, such as 400 or 440, to restrict access to authorized users only.
- Regularly monitor the file for any unauthorized changes and restore from backups if necessary.
Block IPs for Login
Blocking IPs for login involves restricting access to the WordPress login page from specific IP addresses or ranges. This can help prevent brute force attacks by blocking repeated login attempts from malicious actors.
Blocking IPs for login is important because it adds a layer of security to the WordPress login page, reducing the risk of unauthorized access and brute force attacks. By blocking malicious IPs, website owners can protect their login pages from automated login attempts and strengthen overall website security.
To block IPs for login:
- Edit the .htaccess file in the root directory of your WordPress installation.
- Add the following code snippet to block access from specific IPs:
<Files wp-login.php>
Order Deny,Allow
Deny from <IP_Address>
</Files>- Replace <IP_Address> with the IP address you want to block. You can add multiple Deny from directives to block multiple IPs.
- Save the changes to the .htaccess file and upload it to your server.
Limiting XML-RPC access
XML-RPC is a feature in WordPress that allows remote publishing, pingbacks, and other functionalities. Limiting XML-RPC access involves restricting or disabling this feature to prevent potential security vulnerabilities.
Limiting XML-RPC access is important because it can help prevent XML-RPC-based attacks, such as brute force attacks and pingback spam. Disabling or limiting XML-RPC access reduces the attack surface and improves overall website security.
To limit XML-RPC access:
- Install and activate a security plugin like Wordfence or Disable XML-RPC.
- Use the plugin settings to disable XML-RPC functionality altogether or restrict access to specific IP addresses.
- Alternatively, add the following code to your theme’s functions.php file or .htaccess file to disable XML-RPC:
# Block WordPress xmlrpc.php requests
<Files xmlrpc.php>
order deny,allow
deny from all
</Files>Restricting Directory Browsing
Directory browsing allows users to view the contents of directories on a web server if no index file is present. Restricting directory browsing disables this feature to prevent unauthorized access to directory contents.
Restricting directory browsing is important because it prevents users from accessing sensitive files or directories that may contain confidential information or vulnerabilities. It helps protect against information disclosure and strengthens website security.
To restrict directory browsing:
- Edit the .htaccess file in the root directory of your website.
- Add the following line to the .htaccess file:
Options -Indexes- Save the changes to the .htaccess file and upload it to your server.
Prevent Hotlinking
Hotlinking, or inline linking, occurs when another website directly links to images or other media files on your website. Preventing hotlinking involves blocking requests from external websites to access your media files directly.
Preventing hotlinking is important because it helps conserve bandwidth, protects against content theft, and prevents unauthorized usage of your website’s resources. By blocking hotlinking, you can ensure that only your website visitors can access your media files.
To prevent hotlinking:
- Edit the .htaccess file in the root directory of your website.
- Add the following lines to the .htaccess file:
# Prevent hotlinking of images
RewriteEngine on
RewriteCond %{HTTP_REFERER} !^$
RewriteCond %{HTTP_REFERER} !^http(s)?://(www.)?yourwebsite.com [NC]
RewriteCond %{HTTP_REFERER} !^http(s)?://(www.)?google.com [NC]
RewriteRule .(jpg|jpeg|png|gif)$ - [NC,F,L]- Replace yourwebsite.com with your actual website domain.
- Save the changes to the .htaccess file and upload it to your server.
Protecting against SQL injection
SQL injection is a type of web security vulnerability that allows attackers to manipulate SQL queries executed by a web application’s database. Attackers can use SQL injection to bypass authentication, retrieve sensitive data, modify database records, or execute arbitrary SQL commands.
Protecting against SQL injection is crucial because it helps prevent unauthorized access to sensitive data and database manipulation. A successful SQL injection attack can lead to data breaches, loss of confidential information, and compromise the integrity of the entire web application.
To protect against SQL injection:
- Use prepared statements and parameterized queries in your database interactions to sanitize user input and prevent malicious SQL injection attempts.
- Implement input validation and sanitization techniques to filter out potentially dangerous characters or SQL commands from user input.
- Utilize web application firewalls (WAFs) or security plugins that offer SQL injection protection features to detect and block SQL injection attacks automatically.
- Regularly audit your codebase for vulnerabilities and apply security patches provided by your framework or CMS.
Blocking bad bots
Bad bots are automated programs or scripts that crawl websites for various purposes, including web scraping, content scraping, email harvesting, and launching malicious attacks. Blocking bad bots involves identifying and restricting access to your website from known malicious bot IP addresses or user agents.
Blocking bad bots is important because it helps protect your website from unwanted traffic, resource depletion, and security threats posed by malicious bots. Bad bots can consume bandwidth, slow down your website, skew analytics data, and even launch coordinated attacks such as DDoS attacks or brute force attacks.
To block bad bots:
- Identify and monitor bot traffic using web server logs, analytics tools, or specialized bot detection services.
- Create and maintain a blacklist of known bad bot IP addresses, user agents, or patterns using your web server’s configuration files, security plugins, or firewall rules.
- Implement bot detection and mitigation techniques such as CAPTCHA challenges, rate limiting, or JavaScript challenges to distinguish between human users and bots.
- Regularly update your bot blocking rules based on new threat intelligence and emerging bot behavior patterns.
Block Includes
Blocking includes involves restricting access to sensitive files or directories on your web server that should not be directly accessible from the web. This prevents unauthorized users from directly accessing critical files or executing malicious scripts.
Blocking includes is important because it helps protect sensitive files, configuration files, and scripts from unauthorized access or exploitation. By blocking access to includes, you can prevent attackers from accessing critical files that could compromise website security or expose sensitive information.
To block includes:
- Configure your web server or application firewall to deny direct access to sensitive files or directories by blocking requests for specific file types or paths.
- Use file permissions and directory permissions to restrict access to sensitive files and directories on your web server.
- Implement access controls and authentication mechanisms to ensure that only authorized users or processes can access includes or execute scripts.
- Regularly audit your server configuration and file permissions to identify and address any misconfigurations or security vulnerabilities that could lead to unauthorized access.
Limiting access to the wp-admin directory
Limiting access to the wp-admin directory involves restricting access to the WordPress admin area, where administrative functions and settings are managed. This helps protect sensitive administrative features and prevent unauthorized access to the WordPress backend.
Limiting access to the wp-admin directory is important because it helps prevent unauthorized users, bots, or attackers from accessing administrative functions, modifying website settings, or compromising website security. By restricting access to the wp-admin directory, you can reduce the risk of brute force attacks, unauthorized login attempts, and other security threats targeting the WordPress admin area.
To limit access to the wp-admin directory:
- Use .htaccess rules or server configuration directives to restrict access to the wp-admin directory based on IP address, user agent, or authentication credentials.
- Implement additional authentication mechanisms such as HTTP authentication, CAPTCHA challenges, or two-factor authentication to verify the identity of users attempting to access the wp-admin directory.
- Regularly monitor access logs and audit trail data to identify and investigate any suspicious or unauthorized access attempts to the wp-admin directory.
- Keep WordPress core, plugins, and themes updated to the latest versions to patch security vulnerabilities and protect against potential exploits targeting the wp-admin directory.
Other General Best Practices to Improve Website Security

Check for Malware
Malware refers to malicious software designed to disrupt, damage, or gain unauthorized access to computer systems or data. Malware can take various forms, including viruses, worms, trojans, ransomware, spyware, and adware.
To detect malware:
- Use reputable antivirus and anti-malware software to scan your website files and server for known malware signatures.
- Perform regular manual inspections of your website files and directories for any suspicious or unfamiliar files, scripts, or code injections.
- Utilize website security scanning services or online tools to identify and flag potential malware infections.
- Monitor website traffic, performance, and behavior for any signs of unusual or malicious activity, such as unexpected redirects, pop-ups, or unauthorized changes.
If malware is detected:
- Quarantine or isolate infected files and directories to prevent further spread of the malware.
- Remove or clean infected files using antivirus or anti-malware software.
- Investigate the source of the malware infection and take steps to address any underlying WordPress security vulnerabilities or weaknesses.
- Implement additional security measures, such as web application firewalls (WAFs), to prevent future malware infections.
Monitor User Activity
Monitoring user activity involves tracking and analyzing user interactions, behavior, and access patterns on a website. This includes login attempts, page views, file uploads, form submissions, and other user actions.
Monitoring user activity is useful in various scenarios, including:
- Identifying and investigating suspicious or unauthorized access attempts.
- Monitoring user engagement and behavior to improve website usability and performance.
- Detecting and preventing fraudulent activities, such as account takeover attempts or data breaches.
To monitor user activity:
- Use website analytics tools or plugins to track and analyze user interactions, traffic sources, and behavior patterns.
- Implement user activity logging and auditing mechanisms to record and track user actions, such as login attempts, page views, and form submissions.
- Set up alerts and notifications to notify administrators of unusual or suspicious user activity, such as multiple failed login attempts or access from unfamiliar IP addresses.
- Review user activity logs and audit trails to identify potential security threats or anomalies and take appropriate action.
SSL Certificate
An SSL (Secure Sockets Layer) certificate is a digital certificate that encrypts data transmitted between a user’s web browser and a website’s server. It ensures secure communication and protects sensitive information, such as login credentials, personal data, and payment details, from interception or tampering by unauthorized parties.
An SSL certificate is important because it establishes trust, authenticity, and confidentiality between a website and its visitors. It helps secure sensitive data, improve website ranking in search engine results, and build credibility with users by displaying a secure connection indicator (e.g., padlock icon) in the browser address bar.
To obtain and install an SSL certificate:
- Purchase an SSL certificate from a reputable certificate authority (CA) or obtain a free certificate from a trusted provider such as Let’s Encrypt.
- Generate a certificate signing request (CSR) from your web server and submit it to the CA along with the required documentation to verify your identity.
- Install the SSL certificate on your web server and configure it to enable HTTPS encryption for your website.
- Test the SSL certificate installation using online SSL checker tools to ensure proper configuration and functionality.
Backup WordPress Regularly
Regular WordPress backups involve creating copies of your website files, database, and configuration settings to restore in case of data loss, corruption, or website downtime. Backups help protect against accidental deletions, hacking attacks, server failures, and other unforeseen events that could compromise website availability and integrity.
Regular backups are important because they provide a safety net and recovery option in case of website disasters or emergencies. They help minimize downtime, data loss, and business disruption by enabling quick restoration of website functionality and data to a previous state.
To backup WordPress regularly:
- Use backup plugins or services that automate the backup process and allow scheduling of regular backups at specified intervals (e.g., daily, weekly, monthly).
- Choose backup storage solutions that offer secure, off-site storage options to protect against local server failures or data loss.
- Test your backups regularly to ensure they are complete, accurate, and functional for restoration purposes.
- Implement a backup retention policy to manage backup versions, storage space, and retention periods based on your specific needs and requirements.
Manage File Permissions
File permissions control access rights and privileges for files and directories on a web server. They determine who can read, write, or execute files and directories, and at what level of access.
Managing file permissions is important because it helps prevent unauthorized access, modification, or deletion of sensitive files and directories. Properly configured file permissions ensure that only authorized users or processes can access and manipulate files, reducing the risk of data breaches, security exploits, and malicious activities.
To manage file permissions:
- Use the Change Mode (chmod) command or file manager tools provided by your web hosting control panel to set appropriate file permissions for your website files and directories.
- Follow the principle of least privilege by granting only the minimum necessary permissions required for each user or process to perform their intended tasks.
- Regularly audit file permissions and access control lists (ACLs) to identify and correct any misconfigurations, vulnerabilities, or security weaknesses.
- Consider implementing file integrity monitoring (FIM) tools or security plugins that automatically detect and alert you to changes in file permissions or unauthorized access attempts.
Choose Right Host
Different web hosting options are available, including shared hosting, virtual private servers (VPS), dedicated servers, cloud hosting, and managed WordPress hosting.
How to choose a secure WordPress hosting and in which cases:
- Shared hosting. Suitable for small websites with low traffic and limited resources. Cost-effective but may lack performance and security features.
- VPS hosting. Offers more flexibility, control, and resources compared to shared hosting. Suitable for medium-sized websites with moderate traffic and resource requirements.
- Dedicated servers. Provide maximum performance, security, and customization options. Ideal for large websites with high traffic volumes and complex resource demands.
- Cloud hosting. Offers scalability, reliability, and redundancy by leveraging cloud infrastructure. Suitable for websites with unpredictable traffic patterns or scalability requirements.
- Managed WordPress hosting. Optimized for WordPress websites with specialized features, performance enhancements, and security measures. Ideal for WordPress
Conclusion
Cyberattacks can take various forms, such as malware injection and DDoS attacks. Hackers often target WordPress websites due to the popularity of the CMS. Therefore, WordPress website owners must be knowledgeable about securing their sites. Securing a WordPress site is an ongoing task as cyberattacks continually evolve. While the risk is always present, implementing security measures for your WordPress site can help reduce these risks.
If you want to launch a secure website, you can rely on our professional team at IT Monks. We prioritize secure and high-quality code and pay attention to all details ensuring comprehensive site protection. Our innovative approach guarantees a fast, secure, and reliable website every step of the way. With our support team in place, you’ll never have to worry about your WordPress website again – we’ll keep it updated and schedule automated offsite backups along with external security scans, among other essential services.
Contact us by filling out a brief form below. We’ll be glad to discuss your project!
FAQ
- Is WordPress Secure?
WordPress is generally considered a secure platform when properly maintained and updated. However, like any other content management system (CMS), WordPress can be vulnerable to security threats if not managed correctly. It’s essential to follow security best practices, keep WordPress core, themes, and plugins updated, and implement additional security measures to enhance website security.
- How to Check WordPress Website Security?
To check the security of your WordPress website:rnu003colu003ern tu003cliu003eUse online security scanning tools or services to scan your website for WordPress security vulnerabilities, malware, and security issues.u003c/liu003ern tu003cliu003eRegularly audit your website files, directories, and database for any suspicious or unauthorized changes.u003c/liu003ern tu003cliu003eMonitor website traffic, user activity, and access logs for signs of unusual or malicious behavior.u003c/liu003ern tu003cliu003eInstall security plugins or services that offer security scanning, monitoring, and protection features to detect and mitigate security threats.u003c/liu003ernu003c/olu003e
- Do I really need a security plugin for WordPress?
While WordPress provides basic security features, such as user authentication and access controls, a dedicated security plugin is highly recommended for enhancing website security. Security plugins offer additional layers of protection, such as firewall protection, malware scanning, brute force attack prevention, and security hardening measures. They help automate security tasks, monitor website security status, and provide alerts and notifications for potential security threats.
- How much secure is a WordPress website?
The security of a WordPress website depends on various factors, including the implementation of security best practices, regular updates, use of security plugins, hosting environment, and user behavior. A properly maintained and secured WordPress website can be highly secure, but absolute security is not guaranteed. It’s essential to stay vigilant, regularly monitor website security, and proactively mitigate security risks and threats.
Contact
Don't like forms?
Shoot us an email at [email protected]