Enterprise Managed Hosting
Table of Contents
Managed enterprise hosting is the default infrastructure for enterprise websites that operate on CMS-driven platforms, especially those built for high-volume traffic, strict compliance standards, and uninterrupted availability.
These digital environments, whether supporting WordPress-powered publishing hubs or hybrid SaaS-facing infrastructures, operate under performance thresholds where even milliseconds of latency or minor misconfigurations translate into tangible business risk. For such mission-critical properties, managed hosting is an infrastructural necessity.
Managed hosting defines a shift in infrastructure control and responsibility: from in-house teams to dedicated hosting providers. These providers assume operational accountability across the entire hosted infrastructure layer. That means automated OS-level patch deployment, proactive performance monitoring, load balancing, and resource elasticity are delivered as baseline services.
Unlike unmanaged environments, where enterprises must micromanage updates, handle unexpected traffic surges manually, and coordinate backups through fragmented tooling, managed hosting externalizes and centralizes these burdens.
For enterprise websites, managed hosting supports measurable outcomes: 99.99% uptime, SLA-backed security protocols, and built-in compliance capabilities to meet regulatory standards (e.g., GDPR, HIPAA). It eliminates the overhead of manual intervention, enabling DevOps teams to work within CI/CD-aligned environments while keeping the underlying platform stable, secure, and scalable.
By shifting infrastructure operations to the hosting provider, enterprise teams gain the freedom to focus on application logic and user experience without sacrificing performance or compliance integrity.
This redistribution of hosting responsibility is what distinguishes managed hosting from traditional self-managed alternatives. And for enterprise-scale websites, it’s precisely this operational alignment that makes managed hosting a prerequisite.
What Is Managed Hosting for Enterprise?
Managed hosting for enterprise is a system-level operational model where the hosting provider assumes full responsibility for critical backend operations, spanning from uptime monitoring and automated provisioning to security patching and configuration management.
Rather than merely supplying raw compute or bandwidth, managed hosting at this scale abstracts away core infrastructure duties, allowing application teams to focus on delivery without engaging in manual maintenance or firefighting.
For enterprise websites, the managed hosting layer delivers customized infrastructure configurations and provider-managed operations tailored to high-demand environments. This includes server-level configuration, continuous OS-level patching, real-time server monitoring, CDN integration, and database backup orchestration under enforceable service-level agreements (SLAs). The goal is not just to host, but to guarantee performance thresholds, compliance alignment, and operational uptime.
Unlike SMB-level offerings, enterprise managed hosting integrates deeper service dependencies and DevOps-enablement pathways, ensuring compatibility with CI/CD workflows and multi-environment deployments. The provider-level responsibility spans resource provisioning during traffic surges, SLA-based fault response, and compliance-aligned data handling, delivering infrastructure as a governed, living service model.
As such, hosting for enterprise websites functions less as a technical deployment and more as an operational partnership: the infrastructure itself becomes a managed abstraction. This makes managed hosting the default infrastructural layer for performance-sensitive, compliance-heavy, high-volume enterprise digital assets.
Why Enterprise Websites Benefit from Managed Hosting?
Enterprise websites benefit from managed hosting because their infrastructure requirements exceed what internal teams can reliably maintain without incurring technical debt or operational risk. High traffic volume, multi-layered software stacks, and compliance-driven data handling create a level of system complexity that requires externalized infrastructure management to sustain uptime thresholds and service continuity.
At enterprise scale, even minor latency during peak traffic can impact critical transactions or user workflows. These websites depend on scalable infrastructure that adjusts to real-time demand — something managed hosting delivers through automated resource orchestration, elastic scaling policies, and traffic-aware load balancing. Without this, in-house teams would have to manage concurrency limits manually, introducing risk to uptime and user experience.
Technical ecosystems behind enterprise websites often include version-sensitive integrations, custom configurations, and strict environment segregation. Attempting to maintain these manually exposes the organization to configuration drift, patch lag, and security vulnerabilities. Managed hosting mitigates this through structured server monitoring, OS-level patch automation, and SLA-bound performance guarantees tailored to enterprise compliance standards.
Moreover, maintaining internal DevOps alignment while scaling infrastructure across regions imposes staffing and tooling burdens. Managed hosting eliminates internal ops overload by providing CI/CD-compatible environments and integrated monitoring stacks, enabling enterprise teams to focus on application delivery, not hardware oversight.
Compliance enforcement adds yet another layer of complexity. Whether dealing with data residency requirements, audit logging, or industry-specific retention rules, enterprise websites require hosting models that abstract these mandates into provider-managed responsibilities. Managed hosting providers deliver this through automated backups, regional deployment options, and documented compliance workload coverage baked into their service-level agreements.
Core Infrastructure Features in Enterprise Managed Hosting
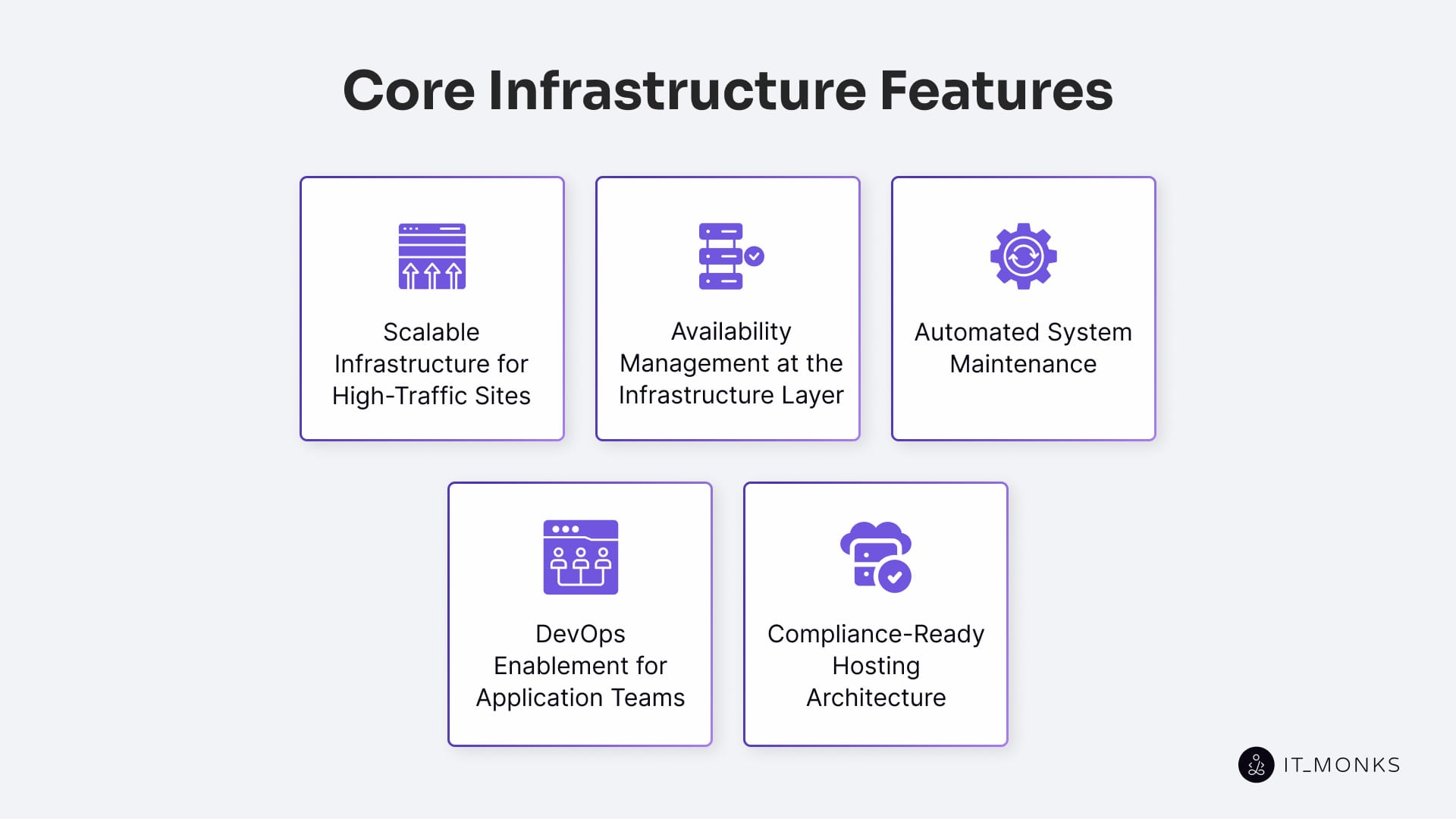
Core infrastructure features in enterprise managed hosting represent orchestrated service components that enable uptime assurance, performance scaling, system automation, and compliance execution at the platform level.
Unlike unmanaged hosting setups, these features aren’t modular options; they’re embedded responsibilities within the managed hosting platform, designed to maintain enterprise-grade infrastructure under real-time operational pressure. To support enterprise websites, the platform must deliver resource scalability, enforce high availability systems, and perform automated server maintenance with minimal latency and zero manual intervention.
This includes technical mechanisms like load distribution protocols, dynamic resource elasticity for demand spikes, and integrated monitoring infrastructure for predictive issue resolution. These systems must also align with enterprise deployment flows (meaning full CI/CD pipeline integration and custom configuration management), while maintaining a compliance-ready environment through automated data backups, regional failovers, and system-level access controls.
Together, these infrastructure modules form a coordinated operational layer that supports service continuity, mitigates technical risk, and enables enterprise teams to operate at scale without direct infrastructure entanglement. The sections that follow break down these dependencies across scaling capacity, availability orchestration, maintenance automation, DevOps enablement, and compliance support.
Scalable Infrastructure for High-Traffic Sites
Scalable infrastructure refers to the automated orchestration of compute resources (CPU, memory, storage, and network throughput) based on real-time demand fluctuations and usage thresholds. Enterprise websites, particularly CMS-driven platforms, routinely experience volatile traffic conditions during product launches, global events, or seasonal campaigns. Without embedded scalability, such spikes strain fixed-resource environments, leading to latency degradation or outright service failure.
The managed hosting platform responds to these conditions by allocating elastic resources, either vertically (enhancing existing nodes) or horizontally (provisioning new containerized instances across availability zones). This process is driven by load monitoring systems that detect rising concurrency, saturation thresholds, or request bottlenecks. By doing so, the platform ensures performance stability across all user sessions while maintaining uptime guarantees and SLA adherence.
Elastic Resources for Handling High-Traffic Spikes
Elastic resources are the dynamic compute, memory, and bandwidth layers that are provisioned on demand in response to traffic spikes or system saturation thresholds. During peak events (like flash sales, media campaigns, or viral content surges), enterprise websites can’t rely on static capacity limits. They require infrastructure that detects usage overload in real time and responds by scaling compute allocations automatically.
The managed platform’s load threshold detection system triggers elasticity events, provisioning additional containers, expanding memory pools, and increasing network throughput to absorb the surge. These adjustments are not manual interventions but are part of a predictive scaling protocol, informed by live metrics and stress patterns.
Once the spike subsides, the system retracts surplus resources, preserving cost efficiency without compromising availability.
Availability Management at the Infrastructure Layer
Availability management is the system-level coordination of failover protocols, load distribution, and health monitoring to guarantee continuous service uptime, even during infrastructure disruption.
The managed hosting platform maintains this availability through redundancy protocols, geo-distributed failover clusters, and real-time heartbeat monitoring. When a node fails or latency spikes, the platform instantly reroutes traffic using latency-aware routing fabric, ensuring uninterrupted service.
These mechanisms are embedded at the infrastructure layer, not applied post-facto, and are governed by strict SLA enforcement metrics..
Load Balancing
Load balancing is the infrastructure-level routing mechanism that distributes incoming traffic across multiple healthy server nodes to prevent overload and maintain performance continuity. As enterprise websites handle high-concurrency sessions from globally dispersed users, the risk of server strain or uneven latency grows with each request surge.
To address this, the managed hosting platform implements intelligent load balancing protocols that monitor server health, resource usage, and latency response times. Traffic is routed based on live metrics, using algorithms that factor in availability zones, failover readiness, and usage saturation. When a node drops or degrades, the system reroutes traffic to optimal zones without impacting the client session. This preserves site responsiveness, supports failover coordination, and maintains SLA-aligned availability. True to form, this infrastructure-level routing logic reflects the role of an enterprise load balancer: it’s not an add-on, it’s an active service continuity mechanism, deeply integrated into the hosting runtime.
Automated System Maintenance
Automated system maintenance is the platform-led orchestration of operational routines, executed without developer input, downtime windows, or human oversight. Enterprise websites require constant patching, monitoring, and remediation to avoid drift, performance degradation, and unpatched security exposures. At scale, this cannot be achieved through manual intervention or reactive support tickets.
The managed hosting platform assumes full responsibility for cron-based maintenance routines that include OS-level patch deployment, security update propagation, service restarts, resource cleanup, and error recovery. These tasks are initiated through real-time health monitoring or pre-scheduled workflows, ensuring infrastructure hygiene is maintained proactively.
By executing these workflows in a non-disruptive, infrastructure-aware context, the platform reduces operational risk, preserves uptime thresholds, and ensures continuous system compliance.
OS-Level Patch Deployment
OS-level patch deployment is a provider-executed security and stability routine, targeting kernel vulnerabilities, package updates, and system-level improvements. For enterprise environments where compliance, uptime, and threat exposure converge, manual patching cycles are a systemic liability.
The managed hosting platform orchestrates these updates through scheduled patch windows, live-kernel patching (where supported), and staged rollout logic—all designed to avoid service interruption while ensuring CVE response coverage and kernel-level hardening. Patches are tracked, version-controlled, and, when necessary, rolled back based on runtime performance signals. This non-interruptive patch orchestration ensures that enterprise applications operate on secure, up-to-date infrastructure without operational input or risk-prone delays.
DevOps Enablement for Application Teams
DevOps enablement is the infrastructure-level abstraction and automation that allows application teams to focus entirely on the software lifecycle (code, test, deploy, observe) without managing servers, configs, or deployment environments. In high-velocity delivery pipelines, manual handoffs, configuration drift, and inconsistent infrastructure become blockers.
The managed hosting platform provides CI/CD-aligned deployment hooks, preconfigured environments, and API-triggered orchestration layers that support every stage of the DevOps workflow.
From automated provisioning of runtime environments to rollback orchestration and config-as-code compatibility, the platform removes infra ownership from the dev side. The result is a DevOps-native hosting model where delivery speed, consistency, and operational integrity are sustained by the infrastructure itself, not by custom scripts or Friday-night server configs.
CI/CD Pipeline Compatibility
CI/CD pipeline compatibility means that deployment automation is built into the infrastructure layer. Enterprise teams rely on version-controlled, Git-triggered release flows, and the hosting environment must act as a native endpoint in that pipeline.
The platform supports automated deployment via webhook integrations, CLI tools, rollback logic, and Git-based branch targeting, enabling developers to push, test, and release without leaving the CI/CD ecosystem.
This system executes builds, logs events, and preserves environment parity across test and production. The outcome is a fully automated, infra-aware deployment flow that accelerates code delivery while minimizing ops overhead and rollback risk.
Compliance-Ready Hosting Architecture
Compliance-ready hosting architecture is the infrastructure-first enforcement of data handling, access control, and auditability standards. Enterprise websites are governed by regulatory frameworks (such as PCI DSS, HIPAA, SOC 2) that demand traceability, access restriction, encryption, and recoverability at the system level.
The managed platform enforces role-based access controls, encrypted data transport and storage, automated backup retention, and isolated runtime environments to maintain an always-auditable posture. Logging is continuous, structured, and retained according to compliance retention policies.
These controls are embedded in the architecture and executed by the provider. This results in a regulation-aligned infrastructure where compliance is systemic, auditable, and enforced by design.
Automated Backup Routines
Automated backup routines are platform-executed snapshots of application data, databases, and configurations, scheduled and stored without any manual intervention.
The platform performs incremental and full backups on fixed schedules or event triggers, encrypting and storing them across geo-redundant infrastructure with strict retention policies and restore protocols.
These routines are monitored, versioned, and aligned with disaster recovery and compliance mandates, providing a continuous rollback point and audit trail. The outcome is infrastructure-level data resilience, ensuring that critical assets are protected, restorable, and verifiably preserved.
How to Choose an Enterprise Managed Hosting Service

To choose the right enterprise managed hosting service, you must align your application’s operational, architectural, and compliance requirements with the platform’s infrastructure capabilities, support guarantees, and DevOps integrations.
Start by understanding that enterprise hosting isn’t a one-size-fits-all solution. Your selection process should assess whether the platform can accommodate your traffic scale, architecture model (monolith vs microservices), CI/CD pipeline, and compliance landscape (SOC 2, HIPAA, GDPR). It’s about stack-specific deployment compatibility, not just OS support. Does the platform provide automation hooks for your team’s delivery model? Can it support observability tooling or staged rollbacks?
Equally important is evaluating the platform’s operational layer: SLAs, support responsiveness, incident escalation, and onboarding. This includes whether they offer migration assistance, enforce performance ceilings, and enable long-term growth trajectory support.
At its core, the decision comes down to fit logic: Does the managed host extend and enable your infrastructure or will it bottleneck it with gaps, manual overhead, or compliance risks?
Choose a partner that integrates with your enterprise stack and evolves with your application. Otherwise, you’re just buying someone else’s maintenance backlog.
Define the Website Needs
Before any hosting platform can be evaluated, the enterprise team must define the website’s infrastructure profile — a scoped set of operating conditions, dependencies, and delivery constraints. This includes identifying traffic concurrency thresholds, stack-specific infrastructure dependencies, and the geographic delivery zone in which the application must perform. Runtime behavior, such as high read/write intensity or request spikes, directly influences the required resource allocation strategy and load routing model.
The team must also specify compliance-hosting overlap, such as GDPR zones or HIPAA-aligned storage, and articulate the deployment cadence and rollback tolerance — whether daily releases or infrequent updates, rollback capability is non-negotiable.
Every selection decision downstream relies on this profile to match real application demands with the provider’s platform capabilities.
Identify Critical Hosting Capabilities for Your Stack
An enterprise-grade hosting platform must align with the stack’s execution model at runtime, build, and scale. That means supporting the exact runtime compatibility matrix — whether PHP 8.2, Node.js LTS, or Python versions are used for job workers. Hosting services must account for stateful storage persistence, container-native orchestration, and I/O-intensive workload support, particularly for DB-heavy or media-rich applications.
Deployment models matter. Teams using CI/CD pipelines, blue-green deployments, or rolling updates require deployment pipeline alignment, including artifact caching, pre-deployment validation, and rollback enforcement. Background job queues, in-memory processing layers, and middleware stacks further require infrastructure behavior alignment if the platform fails to meet any of these thresholds; uptime stability, deployment velocity, and resource efficiency all collapse.
Check Which Type of CMS the Provider Supports
Enterprise CMS deployments come in many forms — monolithic, like WordPress, headless, like Contentful or Sanity, and hybrid models that pair REST APIs with frontend frameworks. The hosting provider must support CMS-specific execution paths, which include plugin orchestration and isolation, theme compilation hooks, and content delivery via API gateway. This isn’t about being able to “install” the CMS; it’s about sustaining it in production under real workloads.
- For headless models, building pipeline compatibility and provisioning an editorial preview environment are critical.
- For traditional stacks, CMS version pinning and rollback protections must be enforced.
- Hybrid systems demand webhook-triggered frontend rebuilds and staging-to-production sync logic.
Check if Hosting Providers Help with Migration
Enterprise migrations are operations, not tasks. They involve full-stack replication across file systems, databases, DNS, and certificates, and require zero-downtime cutover orchestration with rollback paths. Hosting providers must support migration as a managed onboarding execution with tooling for data transfer validation, live state preservation, and DNS and certificate realignment.
The ideal provider either orchestrates the migration through a concierge team or exposes automated workflows via CLI/API, accompanied by integrity assurance logs and staging parity verification. Without these, the risk of downtime, broken dependencies, or post-migration regressions is high. The enterprise application must transition smoothly without disruption, and the host must own the tooling and processes rather than pushing them onto DevOps teams as an afterthought.
Compare the Support Services of Providers
Enterprise systems demand hosting providers that offer structured support services with a tiered response structure, stack-specific engineer assignment, and platform intervention capability. Providers must define incident resolution guarantees, not just “response times,” and execute engineering-aligned support escalation tied to SLA windows.
The support model must include runtime-level error inspection, deployment pipeline issue triage, and the ability to trigger support-assisted rollback processes during production failures. Platform-integrated interfaces, where errors surface directly in dashboards and trigger contextual alerts, signal operational maturity. If the provider can’t own and resolve issues at the infrastructure and application interface, you don’t have support; you have a contact form.
Top Enterprise Managed Hosting Providers
WordPress VIP
WordPress VIP delivers a curated enterprise-grade WordPress platform engineered for performance, compliance, and editorial governance at scale. Unlike general-purpose hosting, it enforces a Git-based CI/CD integration pipeline, backed by automated code reviews and strict plugin approval workflows. This structure transforms WordPress from a flexible CMS into a governed publishing infrastructure.
The platform’s auto-scaling PHP worker infrastructure, global CDN routing logic, and edge-layer content caching are optimized for content-heavy, latency-sensitive applications. Enterprises deploying VIP gain access to compliance-aligned delivery (SOC 2, ISO 27001, FedRAMP, depending on tier) and a governance-driven deployment control model, including rollback protections and staging review gates.
Editorial teams benefit from role-based publishing workflows, content preview environments, and built-in content integrity checks, while developers retain CI hooks and deployment consistency. WordPress VIP is an infrastructure-as-publishing-pipeline, designed for high-traffic editorial stacks and compliance-intensive environments.
Organizations seeking fully-governed WordPress at a global scale (especially in publishing, media, or government) will find VIP to be among the best enterprise hosting providers, precisely because of its infrastructure maturity and control layers.
WP Engine
WP Engine positions itself as a developer-centric WordPress hosting platform tailored for engineering-led teams seeking CI-compatible workflows, frontend flexibility, and performance automation. The platform supports multi-environment deployment chains, Git and CLI-based orchestration, and workflow-agnostic CI integration, enabling rapid, consistent deployment across dev, staging, and production.
Its headless WordPress support is delivered through Atlas, a decoupled architecture that pairs WPGraphQL with Node.js-based frontend delivery. Teams building with React, Next.js, or other modern stacks benefit from API-integrated content models and auto-scaling infrastructure optimized for request concurrency.
WP Engine also delivers plugin governance with manual override, DDoS protection, and edge-layer cache invalidation tuned for high-velocity release cycles. This allows dev teams to focus on shipping features without managing base-layer infrastructure. For hybrid marketing-engineering orgs, WP Engine balances release velocity with structural stability.
The ideal fit is a team that already owns the stack and just needs the hosting platform to synchronize with DevOps, not control it.
Kinsta
Kinsta provides a containerized execution environment backed by Google Cloud Platform, delivering high-performance WordPress hosting with site-specific resource sandboxing. Each WordPress instance runs in a dedicated LXD-powered site isolation container, ensuring zero cross-site resource contention and tighter security controls.
The platform automates built-in server-side caching, Cloudflare-integrated edge delivery, and auto-healing container runtime for consistent high availability. Vertical scaling is handled via PHP worker allocation per site, making the hosting model especially responsive to high-traffic bursts or dynamic content loads.
Dev teams deploying on Kinsta use Git-pull-based workflows, CLI tools, and 1-click staging to production promotion, supporting simplified DevOps without the overhead of full CI pipelines. Monitoring, uptime alerting, and DDoS mitigation are platform-native.
Kinsta is best suited for enterprises, agencies, or ecommerce teams needing GCP-optimized hosting, performance automation, and operational simplicity—without sacrificing tooling access or stack isolation.
Limitations to Know Before You Choose Managed Hosting
Managed hosting platforms prioritize control, uptime, and security, but that control comes at the cost of flexibility. For enterprise teams running custom stacks, legacy systems, or CI-heavy pipelines, these constraints directly shape what you can deploy, integrate, or optimize.
The core trade-off is this: you get abstraction, but lose precision. Most managed environments restrict low-level access, you won’t get root privileges, OS-level configuration, or kernel module control. This is fine for standard apps, but a dealbreaker for teams needing deep system hooks or custom server modules.
You’ll also encounter rigid compatibility ceilings: many platforms enforce plugin governance, limit runtime flexibility, and push opinionated caching or deployment layers that can break dynamic, multi-service, or non-standard app architectures. CI/CD integration may feel locked-down, especially if you rely on custom build stages or non-default tooling.
And then there’s the scaling wall: vertical performance is often plan-bound, tied to PHP worker counts, bandwidth ceilings, or auto-scaling limits that only move if you upgrade your contract.
Limited Low-Level Stack Access
Managed hosting platforms explicitly restrict access to all system-level components, removing root access, disallowing direct OS configuration, and locking down runtime behaviors. This isn’t a soft boundary; it’s a hard execution envelope that prohibits kernel-level tuning, custom module injection, and manual memory/process adjustments.
Enterprise DevOps teams cannot install packages via apt/yum, patch CVEs independently, or customize server-layer configs like NGINX directives, PHP-FPM tuning, or MySQL buffer settings. Even log access is often reduced to the application layer, neutering visibility during runtime failures or deep debugging.
This predefined infrastructure layer is managed entirely by the host, meaning security hardening, service restarts, and environment variables are enforced from above, with little to no override available.
For highly specialized workloads, this limitation may hinder performance tuning or block deployment entirely.
Compatibility Issues with Legacy or Custom Systems
Legacy applications and custom-built systems often collide directly with the opinionated nature of managed hosting environments. These platforms impose fixed runtime versions, restrict plugin/module ecosystems, and limit system-level configurability, making them structurally incompatible with stacks built outside modern DevOps norms.
Codebases that depend on deprecated PHP versions, shell scripts, or compiled binaries frequently break under managed constraints. Frameworks that rely on hardcoded paths, custom cron replacements, or OS-specific daemon behavior may be outright unsupported. Even databases with unique configurations like MyISAM or file-based backends face deployment blocks.
Managed platforms enforce standardized deployment patterns and runtime environments, disabling ad hoc workflows that were once foundational to legacy apps. This often leads to lift-and-break migrations, where an application deploys cleanly but fails at runtime due to unresolvable conflicts.
Without early compatibility validation, enterprise teams risk forced refactors, incomplete migrations, or performance bottlenecks that stem not from poor code, but from mismatched infrastructure assumptions. In short, custom ≠ compatible in a platform-governed environment.
Contact
Don't like forms?
Shoot us an email at [email protected]




