Enterprise Cloud Migration
Table of Contents
The enterprise cloud migration is a process of transferring website data from legacy, on-premise systems or pre-existing cloud platforms to scalable, interoperable environments.
Whether the transition originates from on-premise data centers or involves cloud-to-cloud reconfiguration across providers, the objective remains identical: restructure the infrastructure layer for optimized workload distribution, compliance enforcement, and deployment continuity.
Positioned within the operational continuum of enterprise website development, the migration framework functions as a corrective response to systemic limitations embedded in runtime fragmentation, middleware coupling, and static hosting dependencies.
The enterprise cloud migration unfolds as a composite of subevents: migrating workloads and aligning OS environments define the initial phase; transition events govern middleware decoupling, hosting reconfiguration, and data transfer orchestration; and the result state manifests as a compliant, cloud-hosted system capable of dynamic scaling and service-level continuity.
The migration framework may involve third-party cloud platforms such as AWS, Azure, or GCP, as well as middleware engines and containerization strategies tailored for enterprise-scale deployment.
Application Environment Compatibility
Application environment constrains enterprise website migration through layered compatibility checks across OS, runtime, and middleware components that govern how the system stack integrates with cloud-native architectures.
The initial configuration, defined by host OS versions, runtime libraries, and middleware dependencies, must be aligned to validate enterprise data migration feasibility.
Operating systems and runtime libraries must independently align with orchestration tools and runtime abstraction layers. This compatibility ensures the enterprise system stack remains operable within container orchestration environments.
If a runtime engine lacks compatibility with the cloud provider’s execution layer, deployment strategies become restricted.
Middleware components introduce a second constraint layer, where integration with hosting provider APIs and API compatibility layers enforce compliance. For example, a middleware layer with an incompatible dependency version against the runtime container architecture restricts operational continuity. A mismatched dependency version in the middleware can render the entire deployment scenario invalid.
Application environment compatibility governs whether the system stack can operate within containerization constraints defined by the target cloud provider architecture. When components fail to align, remediation becomes a prerequisite. Each element must independently support configuration within the target cloud to confirm migration readiness.
OS interoperability, runtime configuration, and middleware dependency resolution form the triad for determining environment alignment. Compatibility checks operate as a structured gate: progression depends on complete alignment across all abstraction layers.
If misalignment is detected at any layer, the application environment requires remediation before the enterprise system stack becomes migration-ready.
OS and Runtime Alignment
The operating system forms the base compatibility layer for enterprise web applications by validating whether its kernel version, file system type, and supported drivers align with the targeted runtime configuration for cloud deployment.
If the host OS fails kernel validation against the container engine, dependency mismatches in the runtime environment can block deployment.
The runtime environment, layered over the OS, must synchronize its interpreter version, whether JVM, Python, or Node.js, with container image constraints and cloud virtualization standards. Misaligned OS layers introduce version conflicts that prevent clean containerization.
Interpreter compatibility depends on both the OS abstraction and the application’s dependency tree. If this alignment fails, remediation triggers via platform abstraction: reconfiguring the base image, building custom containers, or isolating the runtime through VM bridging.
This chain, from OS to runtime to execution layer, acts as a validation path for enterprise cloud migration. When each layer conforms to verified compatibility standards, container image consistency and system portability are preserved. Without this, migration halts before deployment is feasible.
Middleware Dependency Handling
Middleware components in an enterprise web architecture enable communication and coordination across distributed services. This layer includes message brokers, application servers, database drivers, logging agents, protocol adapters, and service meshes, each of which requires precise configuration for runtime integration and service cohesion.
Middleware components interact with runtime environments through hooks and APIs, and misalignments can block orchestration, introduce latency, or halt deployments.
Application servers must align with container runtimes; unsupported environments or missing dependencies constrain orchestration. Messaging layers, such as queue brokers, rely on protocol version matching and listener bindings; incompatibility disrupts state propagation and service mesh continuity.
Database drivers, such as JDBC variants, often conflict with cloud-native abstractions, requiring abstraction layers or containerized wrappers to ensure runtime compatibility. Such misalignments cascade upward, limiting orchestration and threatening uptime guarantees.
Middleware handling starts by mapping version lineages against cloud runtime specs. Resolutions include version pinning, emulation, or abstraction. Where overlap exists with managed services, unnecessary middleware is eliminated to resolve compatibility constraints.
Compatibility handlers, from adapters to emulators, must align with orchestration layers that monitor middleware lifecycle states. Without synchronized runtime hooks, even compatible components may fail during rollouts. This shows orchestration depends not just on compatibility but also on lifecycle awareness and dependency timing.
Resolving middleware constraints through adaptation, abstraction, or removal stabilizes the dependency flow, aligns application runtime with orchestration, and upholds enterprise website uptime during cloud migration.
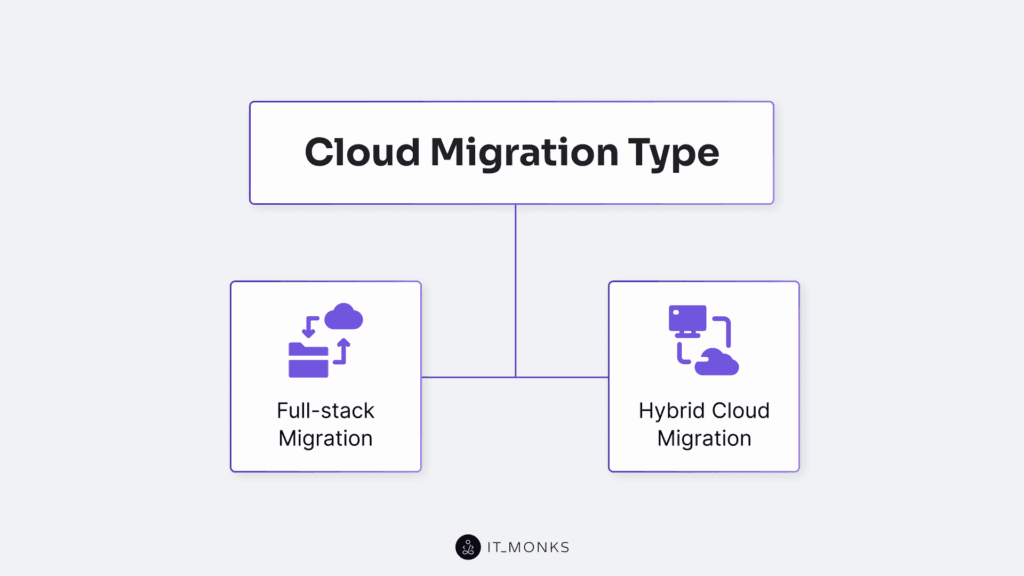
Cloud Migration Type
A cloud migration strategy is a decision layer that determines the scope, continuity, and architectural spread of an enterprise’s move to cloud infrastructure. It governs how the application environment, infrastructure layer, and hosting provider are aligned during the migration event. This strategy directly influences enterprise cloud hosting configurations by establishing the rules for resource placement and orchestration control.
Cloud migration type determines the deployment model by segmenting workloads, aligning infrastructure layers, and constraining orchestration behavior. It defines how application workloads are distributed, how systems are segmented, and how deployment orchestration operates across environments.
The cloud migration strategy is defined by full-stack or hybrid types, each an architectural strategy aligned with deployment models, application architecture, and hosting provider capabilities.
Type selection determines deployment, segments application environments, and realigns platform integration points. It impacts data replication, control plane logic, and resource orchestration.
A full-stack deployment migrates the entire application stack, runtime, middleware, OS, and application logic as a unified system unit. This model enables consistent orchestration and maintains control plane integrity across architectural layers.
A hybrid model segments workload between cloud and on-prem infrastructure. It introduces split orchestration and distributed system states. This type supports selective platform use but increases orchestration complexity and dependency synchronization.
Full-stack Migration
The full-stack migration is an all-inclusive transition of the enterprise web system. The enterprise system architecture transitions entirely to the cloud through a full-stack migration, encapsulating infrastructure, runtime environments, middleware stack, and application layer into a unified deployment. This process begins by abstracting existing infrastructure into modular, orchestration-ready components, ensuring compatibility across all layers.
The infrastructure is restructured into containers, application logic is broken into modular runtimes, and middleware is aligned through version-controlled orchestration. Container orchestration and infrastructure abstraction enforce runtime parity, standardizing deployment across staging and production.
The runtime layer, including variables and dependencies, is aligned with cloud-native templates. Middleware configurations are coupled to runtime constraints, requiring full environment compatibility; misalignment at any layer triggers deployment failure.
The deployment pipeline uses Infrastructure-as-Code (IaC) and config synchronization to maintain state integrity and abstract system boundaries. Platform-specific constraints are handled automatically, ensuring consistent behavior across a single deployment context. Tight layer coupling enhances control but increases sequencing risk.
The hosting configuration adopts full-stack parameters, version-locking each environment setting. Operational readiness depends on exact alignment between configuration intent and runtime behavior; deviations invalidate the entire deployment.
Hybrid Cloud Migration
Hybrid cloud migration is a multi-environmental deployment strategy used in enterprise website transitions. Enterprise application workloads partition the deployment stack during hybrid migration by relocating cloud-suitable components while retaining latency-sensitive or compliance-bound systems on-premise.
Partitioning is driven by compliance mandates, latency constraints, legacy entrenchment, and operational control, all dictating workload placement. This segmentation aligns with enterprise deployment boundaries, enforcing runtime separation.
Web tiers typically shift to the cloud, while data persistence layers remain on-prem, bridged by API gateways and service meshes. These synchronization layers abstract runtime states, enforce version alignment, and preserve data consistency. Middleware ensures transactional coherence across dual environments.
Hybrid setups bridge cloud and on-prem systems through orchestrators and runtime bridging tools, minimizing orchestration drift and failover risks. Communication continuity is maintained via load balancer routing and service mesh-reinforced message relays.
Partitioned workloads inherit deployment logic constrained by compliance enforcement layers. The synchronization layer, composed of version-aware services, integrates state tracking and rollback paths to ensure operational continuity.
Hybrid migration is a strategic deployment divergence that enforces versioned execution, persistent communication, and SLA continuity, while maintaining flexible and environment-agnostic hosting configurations.
Hosting Provider Configuration
Hosting provider configuration is a governing layer in enterprise cloud migration. It takes control during the deployment phase, where the hosting provider executes and maintains the enterprise website’s application environment post-migration.
This configuration defines how systems are deployed, scaled, monitored, and recovered, establishing the operational blueprint. It also shapes resource provisioning, runtime orchestration, and SLA enforcement, directly driving infrastructure behavior and system resilience.
Each configuration protocol enforces architectural boundaries via provisioning APIs, container deployment mechanisms, and availability zone distribution. These elements define how the enterprise deployment environment manages autoscaling thresholds, failover mechanisms, and workload placement.
The orchestration interface varies across vendors, requiring alignment with specific CI/CD hooks and versioning constraints. Such a fragmentation affects deployment hooks, delays rollouts, and increases version drift.
The resource provisioning layer manages workload distribution and enforces redundancy by using zone partitioning and failover placement. In a single-vendor deployment, control is centralized, which simplifies management but reduces deployment flexibility. A multi-cloud configuration adds an abstraction layer that improves flexibility but increases coordination complexity.
Each deployment path impacts both compliance enforcement and infrastructure continuity, requiring architectural trade-offs based on policy and operational priorities. The SLA enforcement defines recovery timing, incident flow, and workload tolerance across regions.
Single-Vendor Deployment
Single-vendor deployment is a closed system configuration that exposes operational continuity, dependency risk, orchestration structure, and migration simplicity tied to using a single cloud provider. This model represents a form of enterprise managed hosting, where the full application stack, runtime, orchestration, middleware, and infrastructure are locked into a single provider’s ecosystem.
Single-vendor deployment simplifies deployment logic through centralized orchestration, proprietary toolchains, and uniform runtime configuration. Provisioning, autoscaling, and storage rely on provider-native interfaces, which accelerate deployment and create operational cohesion.
The hosting provider enforces service dependency by controlling runtime models, orchestration behavior, and middleware alignment. SLA scope binds directly to the provider’s infrastructure, reinforcing platform reliance. A single orchestration interface governs all deployment pathways within a closed execution loop.
Monitoring and scaling adopt platform-specific behaviors, including alert thresholds, performance baselines, and fixed observability limits. The resource quota system restricts workload elasticity and redundancy design.
The application stack is structurally coupled to the provider’s proprietary service mesh. This coupling reduces abstraction across environments and limits workload portability. Any upstream API or runtime change must be mirrored downstream, requiring strict alignment with service-tier policies and runtime constraints. As a result, orchestration decisions must be resolved within a fixed system boundary.
Such a configuration improves cohesion and operational speed. However, it also introduces rigid dependency: the enterprise website operates inside a closed, provider-defined system. Consequently, deployment flexibility is limited, and the platform’s inherent rules and architecture constrain integration options.
Multi-Cloud Strategy
A multi-cloud strategy is a distributed deployment model where the enterprise website operates across 2 or more cloud environments to reduce dependency and enhance resilience. Each execution domain is distributed by the orchestration system through vendor-agnostic interfaces that maintain runtime consistency across environments.
The deployment layer abstracts provider-specific configurations using a service mesh and IaC templates, enforcing environment normalization and cross-platform uniformity. To prevent runtime drift between cloud providers, container registries are mirrored, and configuration files are standardized across all environments.
In dedicated enterprise hosting scenarios, multi-cloud deployment enables regulatory segmentation while maintaining unified orchestration through normalized service layers.
Monitoring pipelines bridge provider-specific APIs to a shared telemetry schema, synchronizing metrics, alerting logic, and logging formats. These telemetry channels operate under unified thresholds to enforce SLA parity despite underlying API heterogeneity.
Application workloads are segmented by provider zone, often based on compliance requirements, latency optimization, or service availability targets. Deployment segmentation is enforced through declarative templates and service discovery mechanisms, creating isolated failure domains while maintaining orchestration cohesion.
The failover mechanism duplicates runtime environments across regions, isolating failure and enabling platform-level redundancy. However, this approach increases configuration overhead and orchestration complexity.
The orchestration system governs multi-cloud behavior through tightly controlled service meshes, environment abstraction layers, and normalized IaC patterns. Without these controls, fragmented deployments risk unsynchronized behavior and operational inconsistencies.
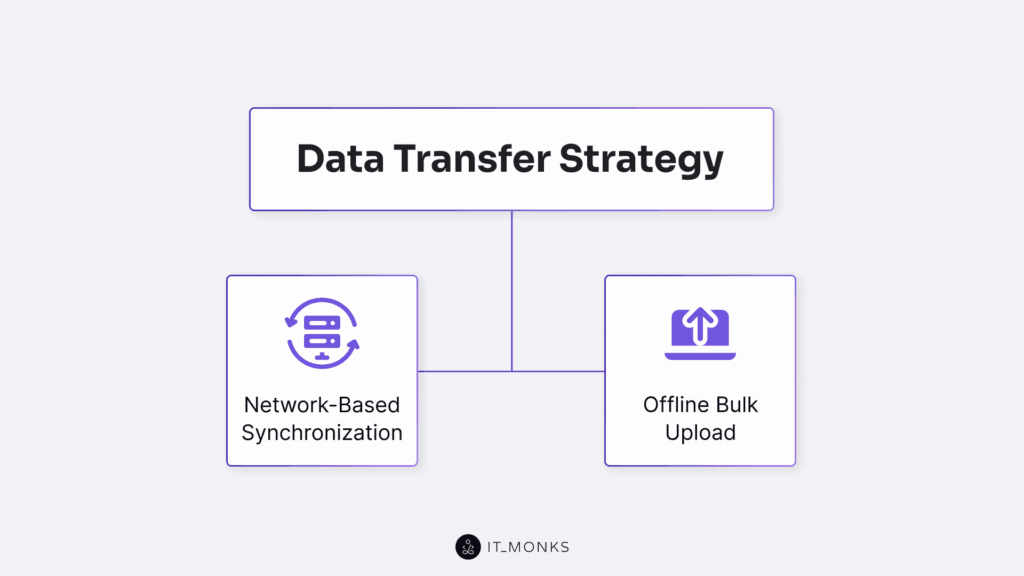
Data Transfer Strategy
A data transfer strategy is a structured, predicate-governed process that enables enterprise website migration by transferring datasets, configurations, and state dependencies from legacy environments to cloud infrastructure. The enterprise data layer governs migration readiness by defining dataset structure, volume, and availability.
A data transfer strategy segments workloads based on schema compatibility, transfer speed, and continuity thresholds. It acts as a predicate-driven model that maps data to cloud ingestion points and constrains transfer timing and method.
Data movement is a pre-deployment event. The transfer mechanism initiates replication cycles and aligns transfer windows with system availability.
Two paths define this process: offline bulk upload, which splits large datasets into ingestible batches via an offline transport medium, and network-based synchronization, which triggers a synchronization controller to replicate data incrementally within bandwidth limits.
Each path includes validation stages. Storage systems apply checksum logic to ensure data integrity. Dataset schemas must align with application runtime compatibility. Synchronization systems enforce latency tolerances to prevent state drift during replication.
The migration orchestration tool aligns bandwidth allocation, replication pacing, and schema compatibility to ensure cutover readiness. Transfer failures compromise deployment viability by corrupting database state or runtime behavior. This strategy secures the final cloud-hosted system.
Offline Bulk Upload
Offline bulk upload is a high-volume, non-networked data transfer method used in enterprise cloud migrations. The enterprise data archive exports the dataset to hardware when the data volume exceeds the viable network capacity or when the replication time overruns the migration window.
Enterprise data archive takes a full data snapshot, encrypts it, and writes it to a physical transfer device using secure media protocols. The snapshot includes schema, structure, and static volume state, packaged for transport in a sealed container.
Physical transfer device initiates an offline ingestion event upon arrival at the cloud provider. Ingestion service triggers rehydration, performs checksum verification, and confirms schema alignment. The validation process verifies completeness and flags any integrity issues before the ingestion pipeline marks the data as ready for processing.
The transfer scheduling protocol aligns this upload with the cutover window. Once ingestion is validated, the system enters a static, pre-deployment state, fully rehydrated, isolated, and awaiting final switchover. Migration cutover plan references this state as the transition point for activation triggers.
This sequence sets a fixed, event-driven path from export to ingest, minimizing transfer variability and enforcing structural boundaries.
Network-Based Synchronization
Network-based synchronization is a continuous or scheduled data replication process used in enterprise cloud migration to ensure state continuity, minimize downtime, and maintain live data availability across environments.
The synchronization system initiates network-based incremental replication to maintain real-time state continuity between the enterprise source and the target cloud environment. Triggered by application data service activity, it uses change data capture (CDC), sync daemons, and distributed queues to mirror changes with delta processing and minimal delay.
Transfer protocols enforce sync intervals and stream data across network channels within defined latency thresholds. The monitoring controller validates consistency through schema checks, replica lag tracking, and event stream analysis. Sync cycles prioritize low-latency ingestion and enforce version parity for uninterrupted application availability.
Once the monitoring controller confirms full schema alignment and version parity under a 300ms lag threshold, the system triggers a cutover checkpoint. The synchronization system halts replication, and the cutover controller finalizes the transition. The migration cutover scheduler tracks readiness based on this parity condition.
Runtime control shifts to the cloud environment, enabling hot cutovers or blue-green deployments without service disruption. The cloud becomes the new primary environment, ensuring continuous availability and supporting failover readiness as part of the migration orchestration process.
DNS Switchover Management
DNS switchover management is a terminal transition event in the enterprise website migration process. The DNS switchover marks the definitive transition point where the enterprise domain record redirects all incoming traffic to the cloud-hosted stack.
This event is governed by timing coordination, TTL enforcement, and resolver propagation cycles. The cutover controller validates the readiness state of the hosting provider and the application layer before triggering any domain resolution redirection.
The TTL configuration engine enforces expiry thresholds, commonly ≤ 60 seconds, prior to cutover. This preemptive TTL reduction minimizes the lifespan of resolver caching, accelerates resolution propagation, and constrains the dual-environment exposure window. Enterprise teams execute this step to invalidate stale cache entries across recursive DNS resolvers and collapse residual routing to the legacy environment.
DNS clients refresh records based on the propagated TTL. A mismatch between resolver refresh intervals and the configured TTL enforces cache drift or fragmented routing. The user routing layer, operating on live resolution data, depends on full propagation across authoritative and recursive layers. Any delay or misalignment results in inconsistent name mapping or degraded access latency.
Once triggered, the switchover finalizes name mapping and exposes the target environment to external traffic. No rollback is possible at the DNS layer. The authoritative nameserver propagates the updated domain bindings, and traffic flow is rerouted in full to the new hosting endpoint. This synchronization must align with application health checks, infrastructure cutover completion, and data ingestion finality.
The enterprise DNS switchover is a resolution-level state transition, not a configuration update. TTL configuration directly governs resolver cache behavior, making timing control essential for synchronized cutover. Mismanagement of TTL, propagation timing, or infrastructure coordination exposes the site to traffic split, delayed access, or complete routing failure.
TTL Reduction Steps
TTL (Time-to-Live) reduction is a pre-cutover operation during an enterprise DNS switchover. The DNS zone file defines and enforces the initial TTL configuration parameter, typically set to 3600 seconds or more, which governs how long recursive resolvers retain DNS records in their caches.
High TTL values prolong resolver cache persistence, causing outdated address data to linger after a switchover, resulting in inconsistent routing and visibility across application environments.
To mitigate this, the cutover scheduler reduces the TTL incrementally, first from 3600 to 300 seconds, then to 60 seconds, beginning several days before the planned migration event.
Each TTL reduction interval is scheduled based on resolver cache expiry cycles, with a minimum of 24 hours between decrements to ensure consistent propagation. This pre-switchover timing sequence synchronizes TTL values with the cutover window, aligning resolution behavior across all DNS consumers.
TTL adjustments are time-bound and force recursive resolvers to revalidate records against the authoritative source. The reduced TTL value shortens resolver cache lifespan, compressing DNS refresh loops into near real-time intervals. This DNS refresh loop enforces re-resolution behavior and mitigates post-cutover resolution delays.
The cache invalidation controller clears stale entries during each interval, compressing propagation lag and tightening resolution accuracy. The authoritative TTL override ensures all recursive resolvers adhere to the enforced refresh schedule, regardless of prior cache state.
Once TTL reaches 60 seconds, recursive resolvers operate in a near-synchronous mode, repeatedly checking the authoritative record to maintain propagation consistency.
This final TTL value aligns DNS record freshness with the switchover window, enabling the cutover scheduler to initiate the authoritative endpoint switch with minimal propagation delay and zero stale resolution.
Cutover Timing Protocol
Cutover timing protocol is a coordinated execution event in enterprise cloud migration, triggered after data ingestion, DNS TTL adjustments, and infrastructure validation have been completed. The migration orchestrator coordinates this trigger event, not as a passive DNS flip, but as a time-bound, system-wide transition.
Execution timing is selected based on historical low-traffic periods, resolver cache expiry estimates, and global propagation latency. This timing is locked only when the TTL expiry aligns precisely with the intended switchover window. The authoritative DNS update is pushed only when TTL expiry aligns with minimal client-side cache retention.
From that point, the DNS resolver system begins shifting queries to the cloud-hosting endpoint, and traffic rerouting proceeds based on measured propagation latency curves. Visibility propagation delay is monitored throughout the switchover window to ensure cache expiration and resolution alignment remain within expected thresholds.
The monitoring controller continuously validates the resolution pipeline for propagation state, response accuracy, and resolver sync state across key regions.
Resolution verification must confirm that the hosting endpoint address is consistently served with accurate propagation before initiating sustained traffic handoff. If propagation lags or inconsistencies emerge, the cutover controller triggers fallback logic, which holds or rolls back traffic based on predefined thresholds.
This protocol defines the cutover not by a scheduled time, but by convergence: TTL expiry, resolution alignment, and infrastructure readiness. Execution is triggered only when these parameters meet at a single deterministic moment. Once the system hands off, the legacy path is no longer authoritative.
Contact
Don't like forms?
Shoot us an email at [email protected]
Send a Project Brief
You need to load content from reCAPTCHA to submit the form. Please note that doing so will share data with third-party providers.
More InformationYou are currently viewing a placeholder content from Turnstile. To access the actual content, click the button below. Please note that doing so will share data with third-party providers.
More InformationYou are currently viewing a placeholder content from Facebook. To access the actual content, click the button below. Please note that doing so will share data with third-party providers.
More InformationYou are currently viewing a placeholder content from Instagram. To access the actual content, click the button below. Please note that doing so will share data with third-party providers.
More InformationYou are currently viewing a placeholder content from X. To access the actual content, click the button below. Please note that doing so will share data with third-party providers.
More Information



