Customization and DevOps Integration in Enterprise Hosting
Table of Contents

In enterprise hosting, customization and DevOps integration define the core capabilities that align automated infrastructure control with deployment-specific adaptability. Together, they establish the primary enabler for delivering stable and scalable enterprise websites.
The enterprise website, with its modular and continuously evolving architecture, depends on a hosting environment that is both programmable and responsive. Within this environment, hosting adaptability extends the initial enabler by maintaining environment parity, preserving configuration fidelity, and enabling safe rollbacks across development, staging, and production.
Building on this adaptability, container orchestration ensures runtime consistency, balances service distribution, and isolates faults to maintain stability. A microservices-ready architecture then segments workloads into independently deployable units. CI/CD pipelines integrate with the hosting layer to automate build triggers, staging promotions, and version-aware production releases. Multi-environment workflows enforce controlled artifact promotion, state tracking, and rollback recovery.
To preserve reliability, Infrastructure as Code (IaC) encodes hosting definitions into version-controlled templates, eliminating drift and ensuring reproducible provisioning. Version control alignment guarantees deployments map directly to branches, commits, and tagged releases. Extending this alignment, GitOps practices enforce declarative synchronization between repositories and live environments. Monitoring and observability close the loop, feeding telemetry, anomaly detection, and rollback validation back into the deployment pipeline.
Through this layered architecture, the enterprise website is deployed, maintained, and evolved by a synchronized mesh of automation systems. The hosting environment becomes an execution partner, coordinating CI/CD workflows, scaling via container-aware scheduling, and securing itself through continuous telemetry.
Hosting Infrastructure Adaptability
Hosting infrastructure adaptability is the ability of enterprise environments to provision resources, synchronize states, and reconfigure workloads consistently across development, staging, and production. For enterprise websites built on rapid iteration and modular services, infrastructure must integrate seamlessly with DevOps pipelines and support runtime changes (such as scaling or configuration updates) without introducing drift or degrading performance.
Adaptable infrastructure ensures environmental parity, replicating configurations across all stages to ensure that version-controlled artifacts behave predictably. This consistency minimizes mismatches, preserves rollback safety, and enables deployments to progress through isolated environments while remaining synchronized. Features such as configuration management and parameter injection strengthen stability across these workflows.
Scalability is a core dimension of adaptability. Hosting systems must respond to demand shifts by dynamically allocating compute and storage resources, keeping services responsive during both steady traffic and sudden surges. Elastic provisioning enables CI/CD pipelines to release new builds and services without disrupting availability.
Adaptability also drives rollback and recovery. By aligning versions across environments and synchronizing state during deployment, infrastructure can quickly reverse failed releases. This reduces friction in pipelines, ensuring that service continuity is preserved even under failure conditions.
Container Orchestration Support
Container orchestration enables hosting infrastructure to manage, schedule, and synchronize containerized workloads reliably across environments. For enterprise websites built from distributed components, orchestration is crucial for maintaining balanced, recoverable services that align with CI/CD pipelines.
Orchestration platforms automate pod scheduling, distribute workloads across nodes, and allocate resources according to service-level demand. This maintains service isolation while supporting both horizontal and vertical scaling. Load balancers direct traffic across container replicas, allowing the website to respond dynamically to demand without sacrificing availability.
Resilience is built in at this layer: failed or degraded containers are automatically restarted, and replicas are redistributed to avoid bottlenecks or single points of failure. Continuous monitoring triggers recovery actions in real time, ensuring service continuity during disruptions.
Orchestration also integrates directly with CI/CD workflows, enabling both stateful and stateless services to be deployed across environments. By aligning runtime states with pipeline outputs, it delivers consistent deployment behavior and rollback safety. Without this orchestration layer, hosting environments cannot provide the responsiveness and stability required for modular, scalable enterprise services.
Microservices-Ready Architecture
A microservices-ready architecture enables hosting environments to segment, isolate, and orchestrate independent service modules, allowing enterprise websites to operate as distributed yet unified systems. This design is essential for executing microservices reliably within CI/CD and DevOps workflows.
Each service runs in its own container, making deployment, scaling, and fault tolerance independent of other modules. Failures remain localized through enforced service boundaries, ephemeral runtimes, readiness/liveness checks, and stateful storage where needed.
Communication flows through API gateways and service meshes, decoupling dependencies and supporting asynchronous interactions. These routing layers preserve discoverability and resilience across dynamic deployments. Environment variables are injected externally through config maps and secrets, ensuring secure and flexible configuration.
The architecture also supports advanced release patterns such as blue-green deployments, canary releases, and hot-swaps, applying load-aware scaling to each service independently. Observability is modularized, with logs, metrics, and traces scoped per service, providing teams with precise visibility into performance and failures.
CI/CD Pipeline Integration
CI/CD pipeline integration couples hosting infrastructure with automated delivery workflows, ensuring that code changes are tested, validated, and deployed across environments with rollback safety and configuration fidelity. For enterprise websites operating under a modular development framework and undergoing continuous updates, this integration is crucial for maintaining consistency, speed, and reliability.
When developers commit code, the CI pipeline provisions automated test environments. It executes containerized test instances, injects environment variables, and validates results through parallelized testing. This process catches errors early, reducing risk before builds reach staging or production.
In staging, pipelines promote validated artifacts into deployments that mirror production conditions. The hosting infrastructure supports this process through configuration mapping, secrets management, and runtime parameter injection. As a result, staging reliably predicts production behavior and prevents drift.
At the production stage, CD pipelines release version-locked artifacts through controlled strategies such as canary rollouts and blue-green swaps. Hosting infrastructure must execute these releases predictably and with full monitoring. Rollback systems utilize artifact version tracking and state awareness to restore stability in the event of failures quickly.
By tightly binding hosting to CI/CD workflows, enterprise websites gain a delivery model that is both continuous and deterministic. Every deployment event (from merge-triggered builds to production releases) follows pipeline logic and is enforced by infrastructure integration. Without this alignment, velocity becomes unstable, rollback integrity weakens, and enterprise-grade hosting risks collapse under uncontrolled change.
Multi-Environment Deployment Workflows
Multi-environment workflows govern the promotion of versioned artifacts through development, staging, and production, with hosting infrastructure enforcing isolation, configuration consistency, and rollback safety at every stage. For enterprise websites operating under constant change, these workflows provide a reproducible sequence for validating and releasing updates.
In the development environment, pipelines provision containerized test instances where new builds are executed automatically. Hosting systems inject environment-specific configs and secrets, ensuring tests reflect real dependencies while keeping unstable code isolated and traceable.
In the staging environment, validated artifacts are deployed into clusters that mirror the production environment. Hosting infrastructure enforces environmental parity by syncing with version-controlled definitions. Techniques such as canary routing and approval gates simulate phased rollouts, while rollback controllers stop faulty releases and revert staging to a stable baseline.
In the production environment, tested artifacts are promoted into live runtime clusters. Secrets and variables are applied at deployment, and automated gates with rollback integration guarantee that if anomalies arise, the system can immediately revert to the last known-good version without affecting availability.
Infrastructure as Code Implementation
Infrastructure as Code (IaC) treats hosting environments as programmable, version-controlled assets. For enterprise websites operating under rapid iteration, IaC maintains environment parity, prevents drift, and ensures rollback safety across development, staging, and production.
Infrastructure definitions are stored in Git repositories, making every state auditable, reproducible, and versioned. Declarative syntax enforces idempotent execution, so deployments produce the same result every time, keeping infrastructure behavior aligned with application pipelines.
CI/CD workflows execute IaC scripts alongside application code, provisioning clusters, network policies, and configurations directly from version control. Each commit or tag maps to a specific environment state, while rollback controllers use IaC state files to restore previously validated conditions with precision.
Replicated templates allow identical stacks across environments, supporting disaster recovery, parallel testing, and multi-cloud deployments without manual reconfiguration. This consistency strengthens both reliability and resilience at scale.
Version Control System Compatibility
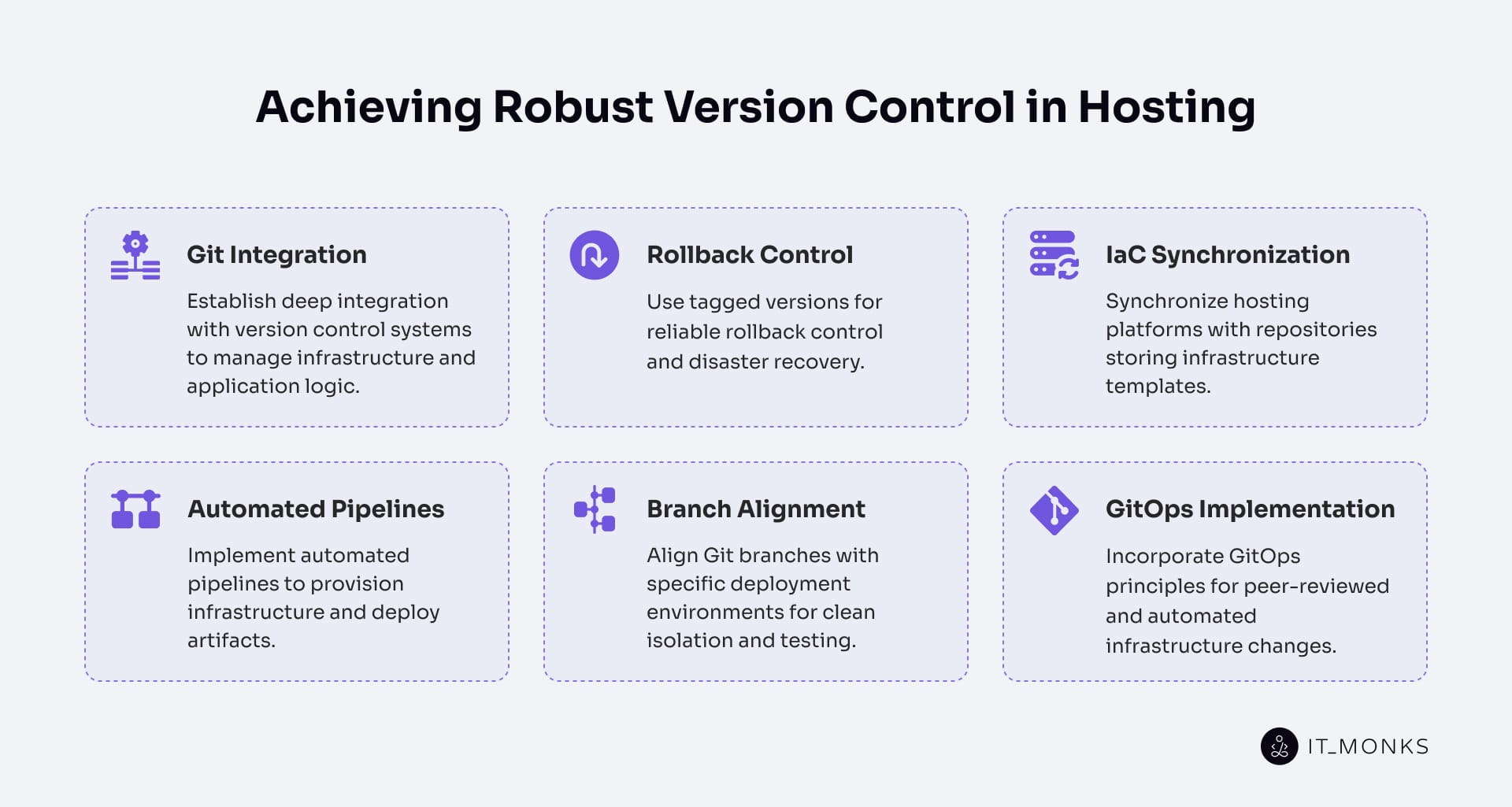
Version control system (VCS) compatibility ensures that hosting environments can synchronize with, deploy from, and roll back to versioned branches, commits, and tagged releases. For enterprise websites, this guarantees reproducible environments, auditable change history, and rollback safety aligned with Git-based repositories.
Hosting must map branches directly to environments, so development, staging, and production each deploy from the correct branch state. Merge-triggered builds then deploy consistently, preventing drift and preserving rollback integrity.
Infrastructure definitions (such as IaC templates, secrets, and config maps) are tracked in version control and resolved at deploy time. This makes configuration injection version-specific and allows rollback controllers to restore environments from tagged commits with precision.
Tagged release workflows enforce stability by deploying from versioned artifacts rather than transient code. Tags act as immutable rollback points and provide a full audit trail for compliance.
GitOps workflows extend VCS compatibility by continuously reconciling live environments with the declared Git state, ensuring seamless integration. This alignment delivers deterministic deployments under load and ensures resilience when scaling enterprise hosting for high traffic.
GitOps-based Release Strategies
GitOps release strategies make the Git repository the source of truth for both applications and infrastructure. Hosting environments synchronize with commits, merges, and tags to deliver deterministic, version-locked deployments. For enterprise websites, this model eliminates ad hoc releases and ensures rollback safety, audit-ready traceability, and consistent environments.
In this approach, every commit or pull request triggers deployment workflows. Branch protections and approval gates control promotion, while the hosting infrastructure reconciles live environments with the declared state in Git. This continuous alignment prevents drift and ensures parity across development, staging, and production environments.
Pull requests serve as release approvals, allowing human or automated checks before promotion. Once merged, the deployment controller applies changes through Git-driven events. Rollback is built in: a revert commit instantly restores the previous state for both code and configuration.
Reconciliation loops keep environments continuously synced with Git, guaranteeing that runtime states match repository definitions. Commit history doubles as a full audit trail, ensuring compliance and governance across deployments.
Monitoring and Observability
Monitoring and observability provide the visibility layer of hosting infrastructure, measuring and correlating system behavior to ensure deployment confidence, rollback safety, and real-time fault awareness. In distributed architectures with dynamic deployments, this layer is crucial for validating performance, isolating faults, and verifying correctness across development, staging, and production environments.
Hosting infrastructure must expose core health signals such as container uptime, resource utilization, and service availability. Telemetry agents collect logs, traces, and metrics from these environments and feed them into centralized platforms. These platforms detect anomalies, trigger alerts, and integrate with CI/CD pipelines to validate new releases and automate rollbacks when regressions occur.
The observability layer also correlates state across components using log pipelines, trace spans, and SLIs. This supports incident containment by pinpointing the exact fault domain while preserving continuity for unaffected modules. For enterprises handling complex traffic loads, organizations rely on monitoring tools for enterprise hosting to maintain stable and resilient services.
Deployment safety depends on these observability capabilities. Monitoring must validate post-deployment behavior and confirm that runtime states match IaC and GitOps definitions. If anomalies arise, rollback controllers respond automatically, minimizing impact. Performance baselines and telemetry also guide intelligent scaling, helping infrastructure adapt to workload shifts while maintaining SLA compliance.
For enterprise-scale systems, monitoring and observability are non-negotiable dependencies. Without them, pipelines lose verification, autoscaling becomes unreliable, and modular architectures risk cascading failures.
Contact
Don't like forms?
Shoot us an email at [email protected]
Send a Project Brief
You need to load content from reCAPTCHA to submit the form. Please note that doing so will share data with third-party providers.
More InformationYou are currently viewing a placeholder content from Turnstile. To access the actual content, click the button below. Please note that doing so will share data with third-party providers.
More InformationYou are currently viewing a placeholder content from Facebook. To access the actual content, click the button below. Please note that doing so will share data with third-party providers.
More InformationYou are currently viewing a placeholder content from Instagram. To access the actual content, click the button below. Please note that doing so will share data with third-party providers.
More InformationYou are currently viewing a placeholder content from X. To access the actual content, click the button below. Please note that doing so will share data with third-party providers.
More Information



